August 17, 2023 | Matt Pacheco
Data Center Physical Security: How to Protect Your Valuable Assets

Despite a greater shift away from on-premise infrastructure and a move toward colocation and cloud providers, IT leaders see data center physical security as a major concern when moving to a third-party data center. Threats like ransomware and DDoS, as well as stringent regulatory requirements, are on everyone’s mind as they seek to maintain control of their company’s data and computing resources. However, those with malicious intent are going to extreme lengths to steal data. Much of the data security conversation revolves around protecting that data from cyber threats, but what about threats to your physical infrastructure?
Data center physical security can be just as important as your cybersecurity. As extreme weather becomes a more prevalent global risk, and data centers become more vulnerable to disasters, both natural and human, service providers should protect against all types of physical security threats.
We’ll cover the key data center physical security features that facilities should have, best practices to maintain security, and other factors to look for in a state-of-the-art data center.
Why is Physical Security Important in Data Centers?
The often-cited open systems interconnection (OSI) model outlines seven layers of a computing system that are subject to potential threats, the first layer being physical security. While all layers need to be addressed, physical security serves as your initial line of defense against incoming threats. Without physical security measures, organizations leave themselves open to easily preventable attacks and vulnerabilities.
Key Data Center Physical Security Features
Each data center will offer distinct security features, but the following are some key items to look for to best protect the first layer of your systems.
Access Provisioning
Access to the data center needs to be provisioned appropriately, meaning no individual or team should have more access than is necessary – employees, vendors, and visitors.
The access provisioning process should actually start before anyone steps foot in the data center. Pre-employment background checks have become nearly universal. Your data center partner should be running them routinely through a third-party vendor with experience in performing background checks for IT employees. They should also perform background checks on vendor and contractor employees who will have access to data.
When a vendor or a contractor needs physical access to the data center, your provider should have policies around access and be able to continually monitor their activity to prevent data theft.
There also need to be procedures in place to change access codes as necessary and revoke all access credentials when an employee with secured physical access leaves the company.
Data Center Security Personnel
Alarm systems and other precautions are a great idea, but the best defense is a good offense. Simply having visible security staff on site 24/7/365 can be enough to thwart an attack before it happens.
Business Continuity and Disaster Recovery
Physical redundancies, including power, cooling, and networking equipment, can improve physical security during a disaster. Data centers can also be considered more physically secure if they include features that withstand floods, fires, or other instances of extreme weather. Geographically optimal locations that are less prone to extreme weather are also better for business continuity.
If your physical location is out of commission due to some kind of outage or disaster, and it’s essential to have some of your staff in the same building, data centers can also offer business continuity via a secondary workspace for business-critical operations.
Video Surveillance
Camera systems can help you catch a criminal in the act and can also help you present critical evidence for an investigation, trial, or insurance claim. At a minimum, your data center provider should have cameras at every entry point to the facility. Fewer windows are better, but if you can’t control that, there should also be cameras on these as they are access points. Security cameras make easy targets for theft as well, so a good data center should digitally archive the data in real time.
Device and Key Management
When your servers are on a rack in an unlocked room, it’s all too easy for someone to lift a server and walk out. A good data center provider will have options that range from a simple PIN or electronic key access to devices and areas of the data center to more sophisticated controls such as multi-factor identification and biometric scans for more sensitive areas of the facility.
Access Logging and Monitoring
Sometimes, how someone is using the access they are given tells a more important story than what access is being provisioned. Data centers that log and monitor access can better identify unusual patterns of behavior that may indicate a potential risk to physical security.
Compliance and Governance
Data center physical security is also a matter of compliance. Industry standards and government regulations, such as PCI DSS, don’t assign different penalties based on whether personal data was stolen by cybercriminal or by a thief who broke a window in the middle of the night. Select a provider that complies with regulations and regularly undergoes compliance audits. A provider with knowledge of compliance regulations is critical to your data security.
Threat Assessment
Physical threats are just as likely to come from within your organization as from external individuals with malicious intent. There are two types of physical threats: the theft of hardware (often for purposes of stealing the data residing on that hardware) and physical attacks designed to sabotage a data center. A good data center provider knows how to properly define and assess these threats.
Best Practices to Keep Data Centers Physically Secure
To keep a data center physically secure, providers should be mindful of the risks associated with visitor access, overprovisioning, malicious activity, and environmental conditions.
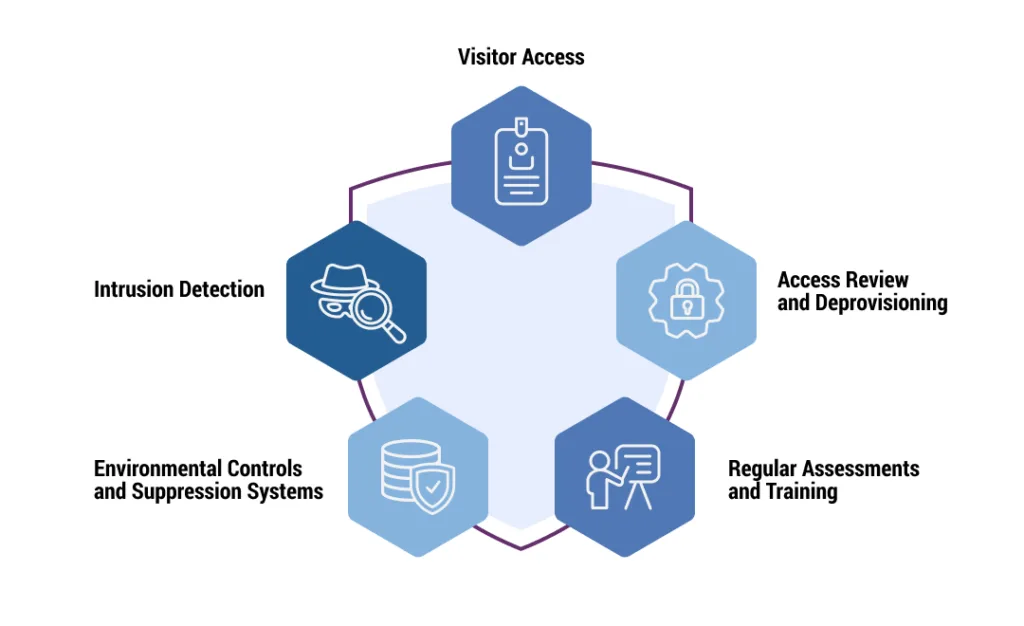
Visitor Access
Visitors should only receive access to the necessary parts of a data center through pre-ordained controls and proper monitoring. Secure data centers can help organizations define the levels of access needed based on the type of visitor to avoid confusion and mitigate risks.
Intrusion Detection
Intrusion detection systems (IDS) should be used to identify unauthorized access to the data center, alerting security personnel to incidents. These can include video surveillance systems, alerts that go off when doors or windows are accessed without authorization, and digital detection systems that evaluate unusual or malicious activity.
Access Review and Deprovisioning
Offering access to visitors, employees, and vendors is not a one-time process. Access should be reviewed on a regular basis and be deprovisioned for permissions that are no longer needed. For example, a team member may need additional access to finish a project, but once that project is complete, it may make sense to adjust and do some deprovisioning.
Environmental Controls and Suppression Systems
The environmental controls in a data center should be set to control temperature, humidity, and power in the facility. Sprinklers and fire extinguishers should also be distributed throughout the data center to suppress any fires.
Regular Assessments and Training
Outside of access review, data centers should be regularly conducting security assessments to identify current risks and plan implementation for new security measures and training to get employees up to speed on new best practices.
Choosing a Physically Secure State-of-the-Art Data Center
Secure colocation with TierPoint allows you to put your company’s IT infrastructure in our strategically located, state-of-the-art data centers. Our facilities are independently audited to ensure we have the controls, processes, and physical security features to help clients get certified as compliant with critical regulations including HIPAA/HITECH, GLBA, PCI-DSS v3.2, and ITAR.
You can read about each of our data center locations to take a closer look at their attributes, including physical security features. When you’re ready, you can also request an on-site tour.

