
Cloud migration projects can be beneficial to an organization in many ways. This includes leveraging the robust infrastructural cloud migration security measures provided by cloud providers. However, keep in mind that neither on-premise nor cloud environments are immune to security issues. Plus, migrating to the cloud doesn’t mean that cybersecurity becomes the cloud provider’s responsibility. In fact, the number one investment priority for global enterprise cloud decision-makers is cybersecurity.
Understanding the key safety insights for cloud environments, especially how they compare to on-premise environments, is an important part of keeping your organization safe. We’ll cover the differences between on-premise and cloud security, as well as some key steps to ensure safety in the cloud.
The Importance of Security in Cloud Migration
If your business is planning a cloud migration, particularly moving your on-premise workloads to a public cloud provider, it’s vital to understand the security implications and changes when your workloads move to a third-party vendor. While cloud providers offer a range of security measures designed to protect their infrastructure and services, it’s important to recognize that various vulnerabilities and threats remain the responsibility of your business to monitor and mitigate. Therefore, gaining a deep understanding of security considerations in cloud migration is absolutely essential.
Cloud Migration Security Challenges
In the realm of cloud migration, security takes on a complex and multi-layered nature. While cloud providers bear the primary responsiblility of maintaining and safeguarding the underlying infrastructure, they’re not impervious to cyber threats or attacks and overall security remains a shared responsibility. To ensure a comprehensive security posture in the cloud, organizations should actively manage:
- Application-level security
- Access controls
- Configurations
- Among others
The shared responsibility security model underscores the significance of understanding and addressing the diverse security challenges that surface when an organization moves its workloads to the cloud.
Shared Responsibility Model
Cloud migration involves a shift in the responsibility for certain security aspects. Cloud providers are responsible for securing the underlying infrastructure, data centers, and foundational services. However, your organization retains responsibility for securing the applications data, configurations, access controls, and compliance with industry standards. This shared responsibility model necessitates a clear understanding of where the provider’s responsibilities end and yours begins.
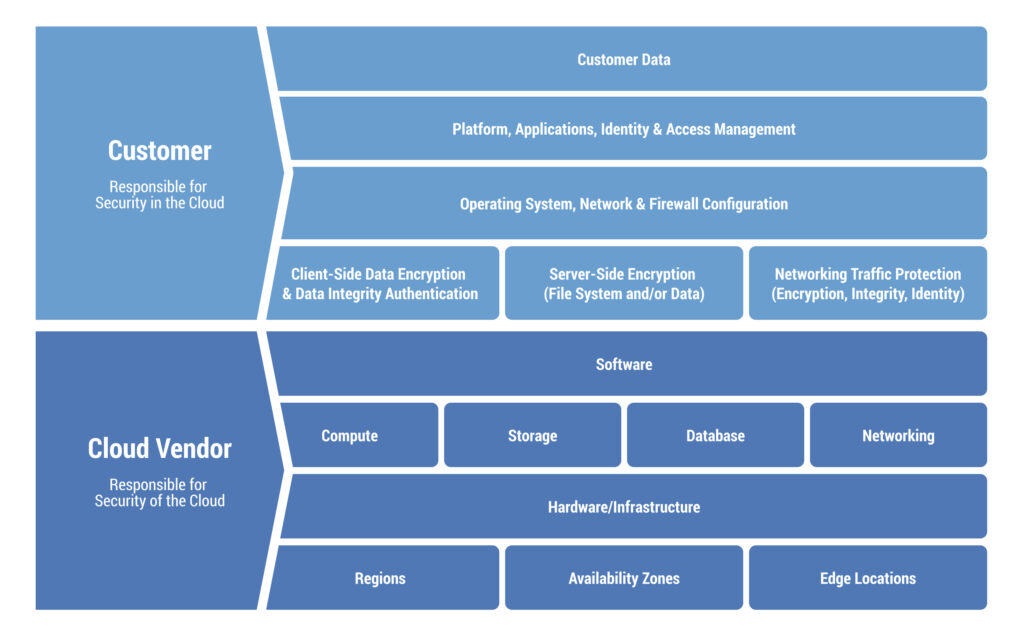
New Threat Landscape
The cloud introduces a new threat landscape that requires careful attention. Threats such as unauthorized access, data breaches, and cyberattacks can potentially lead to severe consequences. The dynamic and scalable nature of cloud environments means that traditional security measures might need adjustments to match the cloud’s agility while maintaining robust protection.
Cloud Security vs. On-Premises Security
When businesses have their data and applications in an on-premise environment, they are in control of protecting the data, and may even have customized security solutions in place for the processing and storage of data and applications. On-premises security measures give organizations complete control over the security of their workloads.
Conversely, cloud security requires cloud providers and their clients to be mutually responsible for the security of their systems. Providers mainly watch over the physical aspects of security, and the security of the underlying network infrastructure . Organizations hold most of the responsibility for their applications and data being housed in the cloud.
Key Elements of Cloud Migration Security
Risk Assessment and Planning
Before migration, conduct a thorough risk assessment to identify potential security risks and vulnerabilities. Create a migration plan that includes security considerations to mitigate these risks effectively.
Configuration Management
Ensure that cloud resources are configured securely. Follow best practices and guidelines provided by the cloud provider to avoid misconfigurations that can lead to vulnerabilities.
Backup and Disaster Recovery
Implement robust backup and disaster recovery strategies to ensure business continuity in case of data loss or service disruption.
Data Encryption
When data is encrypted, it’s unable to be read by unauthorized users because it’s scrambled. Secure data should be encrypted both at rest and in transit.
Identity and Access Management
Not every user needs the same level of access. Some users may need administrative access to certain environments, whereas others won’t need authorization at all. Understanding necessary levels of access and doling them out appropriately can limit the risk that comes from application and data access.
Incident Response
If a security incident happens, a plan should already be in place for how to respond. How will incidents be found, contained, and addressed? Be sure to implement continuous monitoring so security threats can be detected and handled quickly.
Compliance
Major cloud providers are compliant, or can be compliant, with major regulatory standards like HIPAA. However, some additional features or configurations may need to be added for environments to be considered compliant. Organizations should understand regulatory requirements in the cloud, and the changes that may need to be implemented when moving from an on-premises environment.
Vulnerability Scanning
The cloud environment should be scanned during and after cloud migration for vulnerabilities. Especially when major changes are made, this can help find and solve any security concerns.
How to Mitigate Cloud Migration Security Risks
Many cloud migration challenges, including security risks, can be significantly reduced by periodically revisiting access controls, organizational responsibilities, business-wide safeguards, and more.
Access Control
Implement the principle of least privilege to limit access to only what is necessary for each user’s role. Downgrade or decommission access when it’s no longer needed.
Automation
Automating processes can cut down on manual errors. Any steps in cloud migration and management that are repetitive may be able to be handled by an automated ruleset.
Visibility
The more you gain visibility over your cloud environment, the more you’ll be able to identify suspicious behaviors and protect your systems from cybersecurity attacks. Some security tools can present data from multiple cloud environments, but make sure whatever you use has a comprehensive view of your entire IT landscape.
Responsibility
It’s the responsibility of the organization to protect its data and applications, but roles within the organization can vary. Whether you’re working with outside cybersecurity experts or not, you’ll want to assign responsibilities for configuring security controls, monitoring, responding to security incidents, educating employees, and communicating with internal and external stakeholders.
MFA
Multi-factor authentication requires all users to provide more than one source of authentication for logins. For example, a user may log in using a name and password but will also be required to verify their identity using an app on their phone or by inserting a physical key.
According to Okta, MFA adoption was at around 64% in January 2023, with 90% of administrators using the method to sign in. This means that a major source of vulnerability for organizations still comes from users who have not opted in to multi-factor authentication. Requiring MFA can substantially reduce the risk of unauthorized logins.
Make Cloud Migration Security a Priority with TierPoint
Taking on a cloud migration project is stressful enough. Security shouldn’t be a worry added to your list. Working with experts who are skilled in both cloud migration and cybersecurity can keep you focused on cloud innovation instead of looking over your shoulder, worried that you forgot about a key vulnerability.
From cloud readiness, to moving legacy apps, to cloud migration security, TierPoint has services and solutions to help. Need help starting your migration? Get the Journey to the Cloud eBook.

