
Cloud storage can greatly improve accessibility to data, allowing teams to collaborate better and more conveniently. However, cloud technologies also come with security risks, especially when multiple users regularly access cloud storage services. We’ll cover best practices for cloud storage security in the face of common threats.
What is Cloud Storage Security?
Cloud storage security includes technologies and practices businesses use to protect their data in cloud storage solutions. This can consist of safeguards against theft, deletion, unauthorized access, or file corruption.
Why is it So Important?
Some security issues are the same between cloud storage and on-premises frameworks. However, moving to a new environment can pose new risks and compliance complexities. Organizations should understand their risks and responsibilities for keeping data safe in the cloud.
What are the Risks of Cloud Storage Security?
While cloud storage offers ease of use and simple scalability, it can also come with new risks that can be more common in the cloud. Here are some of the top cloud-related security threats and risks to keep on your radar.
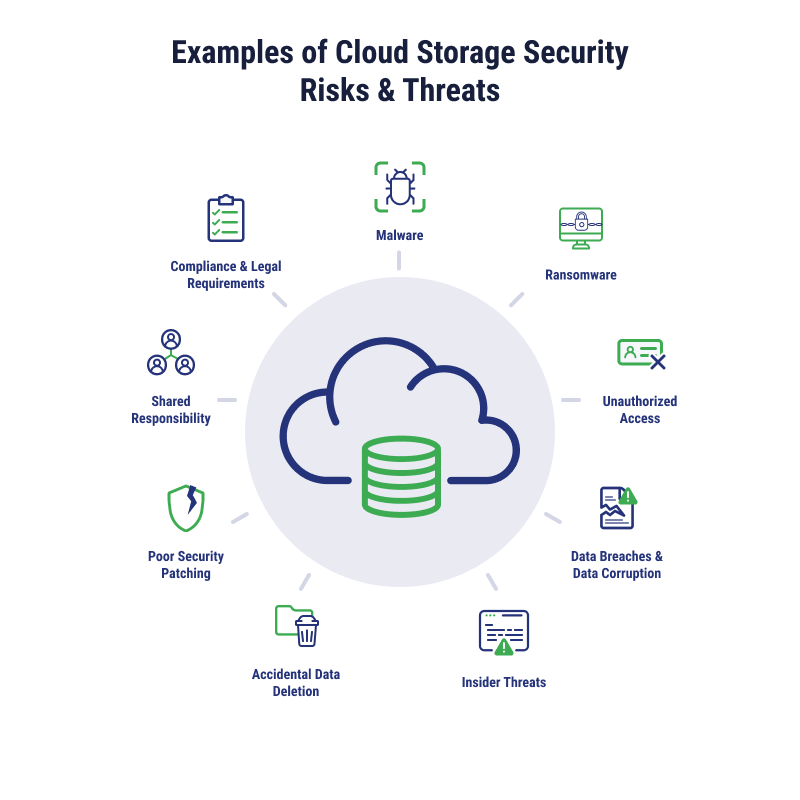
Malware and Ransomware
Organizations of all sizes need to be prepared against ransomware, which accounted for one-quarter of all data breaches in 2023. With ransomware, a user will click on a malicious link in a phishing email, download the wrong link, or neglect to update their software for known vulnerabilities, giving the attacker access to their systems. Once inside, a cybercriminal will encrypt files or lock the user out of their device, demanding a ransom for decryption or access.
Ransomware can often be used with malware, which is malicious code that can infiltrate cloud storage and infect files, steal data, and encrypt as part of the ransom.
Data Breaches, Corruption, and Unauthorized Access
Bad actors gain access to your confidential, sensitive, and valuable information through data breaches. While ransomware is one method cybercriminals may attack the software supply chain or enter through a business partner. Initial attack vectors can include zero-day vulnerabilities, cloud misconfigurations, system errors, or even malicious insiders. The most common starting attack vectors in 2023 were phishing and stolen or compromised credentials.
Insider Threats
Employees within a company can sometimes pose a data security threat and misuse, steal, tamper with, or leak valuable or sensitive data. Approximately 6% of data breaches start with malicious insiders, so while they are not as common as phishing or stolen credentials, inappropriate use and access from inside employees can be a material threat.
Accidental Data Deletion
Cloud storage data deletion can also be completely accidental. Team members may press the wrong button or think data should be deleted without realizing its importance. Without a backup in place, this can severely impact business performance or reduce trust in the company’s security. Accidental data loss happens with about the same frequency as malicious insiders, costing businesses $4.46 million on average.
Poor Security Patching
A zero-day vulnerability is a previously unknown software security risk that attackers can use to exploit your systems. Patching software at regular intervals can substantially reduce this risk. However, users may ignore updates if they aren’t mandatory. IT teams also need to stay vigilant to prioritize critical patching. Known, unpatched vulnerabilities are responsible for about as many data breaches as malicious insiders and accidental data losses.
Shared Responsibility Model
Businesses that migrate data to cloud storage need to be aware of the shared responsibility model and the role they play in keeping data safe in a cloud environment. Cloud providers like AWS will implement infrastructural security measures, but businesses still need to secure their data within the platform through strong access controls, robust password policies, and encryption.
Compliance and Legal Requirements
Some industries and types of businesses will be legally mandated to implement certain data security protocols. Understanding the compliance obligations for cloud data storage can help businesses avoid fines and sanctions while keeping data safer.
7 Cloud Storage Security Best Practices
While organizations may take many approaches to protect data, here are seven best practices to follow to enhance cloud storage security.
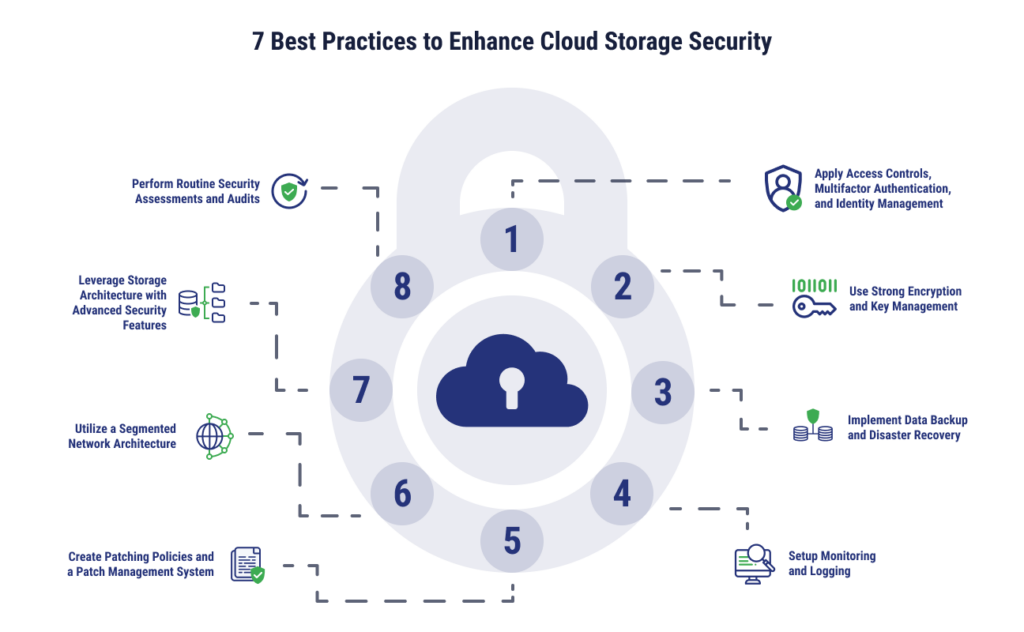
Access Controls, Multifactor Authentication & Identity Management
Access controls determine who can access data and what actions they can take with the data – reading, writing, and deleting, for example. Multifactor or two-factor authentication determines and adds steps a user needs to take to log in, which can include an authentication key, a physical key, and using multiple devices. Identity management is a system businesses can use to set access permissions in cloud storage based on user identities.
Encryption and Key Management
Data should be encrypted at rest and in transit, which means it should be scrambled when moving between points, as well as when it is in cloud storage so that it cannot be read without a decryption key.
Encryption keys used on the data should also be stored with a key management system to prevent unauthorized access.
Backup Data & Implement Disaster Recovery
Data that is only available in one place will always be more vulnerable than data that has a backup somewhere. Regularly backing up data to a separate location, especially one that is geographically distinct, can protect businesses from data breaches, natural disasters, accidental deletion, and more.
A disaster recovery plan should include a strategy for data backups, but should also outline how a business will restore data and applications after an outage or major security incident. This may include switching to another system automatically or manually and should detail the parties responsible for ensuring the backup works and testing it regularly.
Monitor and Log
Unusual behavior can be a sign of malicious activity, such as logging in at odd times or users attempting to access parts of the system that they don’t normally use. A monitoring tool can identify unusual file modifications or unauthorized login attempts. Logging can track user activity for auditing purposes, which can help trace suspicious activity or analyze an incident after it’s been identified.
Patch Management System
Vulnerability management through a strong patching policy can reduce the threat of zero-day vulnerabilities without requiring much effort. Set a patching policy with a schedule for making updates – this might be once a month or once a week, depending on the criticality of the data available in your cloud storage. For example, Microsoft has Patch Tuesday on the second Tuesday of every month. Businesses may also implement a patch management system, which may include automated steps to ensure patching is done routinely.
Segmented Network Architecture
Moving from an on-premises to an off-premises cloud storage solution may feel like you’re migrating data into one large pool. However, there are steps you can take to segment data. Network segmentation is where businesses divide their network into segments to isolate more sensitive data, keeping it separate from areas that are publicly accessible. This can reduce the harm caused by security breaches.
Storage Architecture with Advanced Security Features
To make your cloud storage more secure, you can use storage infrastructure with advanced security features such as:
- Immutability: Ensures data stored in the cloud cannot be modified or deleted, providing protection against ransomware and data breaches
- Secure multitenancy: Enables providing the security of a dedicated environment with the cost-efficiency of a shared storage environment
- Comprehensive security solutions: Including security and business continuity, managed networks, and guided by a team of experienced IT professionals
Routine Security Assessments and Audits
On a high level, organizations should look at their systems periodically to identify new vulnerabilities that may call for additional IT security measures. Businesses may also want to bring in outside professionals to audit their cloud storage security if they lack in-house expertise or don’t have enough time to review their cloud security posture.
Building a Strong Cloud Storage Security Plan
Boosting your cloud storage security posture starts with a solid plan incorporating solutions with advanced security features, such as ransomware protection with immutability or Dedicated Storage as a Service powered by Pure Storage. Need help creating a plan? TierPoint’s IT security consulting services can help you create a strategy and execute it to protect your data both in the cloud and in transit. Contact us to learn more.

