Published: January 12, 2026 | Last Updated: February 5, 2026
What Is Cyber Threat Hunting?

Table of Contents
Rapid response is critical when cyber threats strike, but a proactive approach is even more powerful, helping organizations disrupt attacks before cybercriminals infiltrate critical systems. Cyber threat hunting often begins before confirmed alerts or known incidents arise, with experts proactively searching for subtle indicators of compromise that traditional security measures or automated controls may overlook.
We’ll cover what cyber threat hunting is, common methodologies, how the process works, key technologies used in threat hunting, and what challenges businesses can encounter after implementation.
What Is Cyber Threat Hunting?
Cyber threat hunting is a proactive, investigative process in which skilled cybersecurity professionals search across telemetry, endpoint and system state, and network traffic to find, analyze, and isolate threats that were previously unknown or escaped detection from common security tools. These threat hunters operate like skilled detectives, looking for faint clues and hints of footprints around your systems to identify signals and digital footprints that reveal an adversary actively reconnoitering, staging, or preparing to strike.
With average breach lifecycles still exceeding 200 days, threat hunting is crucial for reducing the time threat actors can spend undetected in an environment. Catching cybercriminals at the beginning of the attack cycle can significantly reduce the fallout of incidents or prevent them entirely.
Threat Hunting Methodologies
Instead of engaging in a single process, threat hunters often implement a combination of methodologies to find and contain potential incidents.
Hypothesis-Driven Hunting
Hypothesis-based hunts take a structured approach that is more proactive for known threats. The process often starts with known adversary tactics, techniques, and procedures (TTPs) that have been documented by frameworks like MITRE ATT&CK. These can be used to form hypotheses around indicators of attack (IoAs), which can include identified TTPs. Examples of IOAs include lateral movement, privilege escalation, or data exfiltration.
A hypothesis formed in this type of testing might look like assuming that a threat actor is using a particular approach to complete a malicious action, then searching log data to find evidence of the hypothesis. Starting with known threats can eliminate issues that could arise from common attack vectors.
Intelligence-Based Hunting
Intelligence-based hunting is less rigidly structured, more exploratory and open-eneded, making it ideal for finding unknown or emerging threats. Security analysts use key data sources, like cyber threat intelligence and security information and event management (SIEM) tools, to understand vulnerabilities and indicators of compromise (IoCs). IoCs may include IP addresses, hashes, and domain names that are associated with threats.
When a threat hunter finds an IoC, they can do a deeper dive into the anomaly, guided by human intuition, even if the incident occurred in the past. An unstructured hunt can spark future hypothesis-driven investigations by uncovering new threat patterns.
Situational Hunting
Situational hunting is focused on specific risks that increase the likelihood of targeted attacks. This method can be event-driven or entity-driven, focusing on specific users, devices, or systems. As such, it relies on the internal context of the organization being protected. The narrow scope might be initiated based on the following triggers:
- Mergers & acquisitions: Merging networks may result in users, including insider threats, gaining unauthorized access to data. Malicious actors may also aim to take advantage of vulnerabilities during the transition.
- Personnel departure: If someone left on bad terms, there may be unusual file access or data exfiltration.
- Executive travel: Monitoring devices and accounts during high-profile travel events can prevent the targeting of executive devices that carry sensitive information.
- Asset changes: Newly deployed critical servers or other high-value assets may trigger new threat hunting initiatives
How Does Threat Hunting Work?
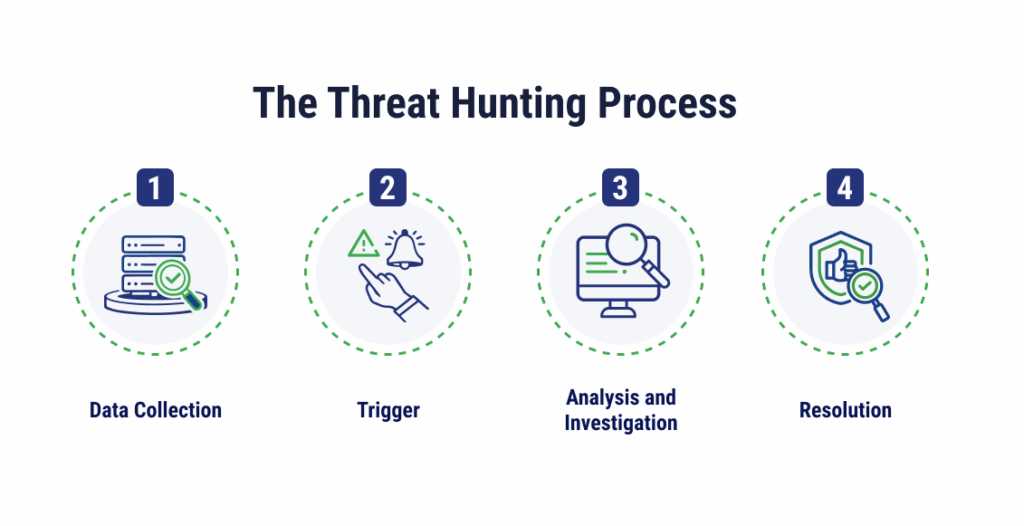
Regardless of the methodologies used, threat hunting follows a similar process of data collecting, responding to a trigger, investigating, and resolving the threat.
Data Collection
Comprehensive, high-quality data is essential for effective threat hunting. Hunters collect endpoint data, network data, and application logs from various sources, including information on file modification, flow data, authentication records, and DNS requests. Having centralized platforms, such as SIEM and data lakes, can make it easier to collect, store, and normalize the data available, making it easier to search and analyze later.
Trigger
Triggers are any actions that begin the threat hunting process. These can be structured or unstructured, and internal or external. For example, with a hypothesis-driven methodology, a trigger can be a new TTP that is popping up in the industry. From there, hunters can form a testable hypothesis, which brings more focus to the investigation stage.
Analysis and Investigation
In the analysis and investigation stage, threat hunters will work to validate the hypothesis through analysis of collected data. This can include using SIEM data to spot anomalous login times or geographic locations, uncover connections with suspicious IPs, or identify unusual processes being carried out with elevated privileges. When suspicious activity is found, threat hunters move to the analysis stage, confirming whether there is any malicious intent in the activity.
Resolution
In the resolution stage, organizations can confirm the threat (true positive) and move into the incident response (IR) process, in which threat hunters will work with teams to contain, remove, and recover from the malicious activity.
It is possible that threat hunters will also find false positives or even no evidence of a true threat. This can result in refining hypotheses for future tests, strengthening defenses, and removing criteria that may otherwise trigger false alarms in the future.
Tools and Technologies Used in Threat Hunting
Proactive threat hunts are always human led, whether conducted by internal security teams or managed detection and response (MDR) service providers. However, analysts can be greatly aided by tools and technologies that can collect, query, and analyze massive amounts of data.
Security Information and Event Management (SIEM)
SIEM systems can serve as powerful central repositories for threat hunting. They collect and normalize threat logs from all sources in your environment so they can be interpreted within a singular platform. This is a macro-level tool that can identify real-time threats and analyze previous activity to establish baselines of what normal behavior looks like.
Endpoint Detection and Response (EDR)
Endpoint detection and response provides a more granular look at activity on individual devices, or endpoints. EDR agents continuously collect and analyze rich endpoint telemetry, including process behavior, file changes, and network activity. This enables security teams to detect and investigate potential malicious behavior across laptops, servers, mobile devices, and other endpoints.
For more comprehensive visibility, threat hunters may alternatively use extended detection and response (XDR) that include EDR capabilities while pulling data from across the cloud, networks, email, and beyond.
AI-Powered Analytics
Manual hunting can feel impossible with how much data IT environments can generate. Artificial intelligence and machine learning (AI/ML) tools can integrate with SIEM, EDR, and XDR platforms to enhance the efficacy of human hunters by spotting anomalies, prioritizing investigations, and performing behavioral analysis with subtle changes that may be undetectable to human observers.
Instead of relying on standard AI-driven querying, threat hunters operationalize AI through custom models and orchestrated workflows that embed threat hunting logic, domain context, and analyst decision-making. This approach captures proven expertise and applies it consistently, delivering repeatable outcomes that go beyond generic, prompt-based AI tools.
Why Is Threat Hunting Important?
The rise of cyber threats increases the risk of missed vulnerabilities and the possibility of hidden threats lurking in your environment. Even when businesses get automated alerts, unknown threats can go undetected by deviating from recognized patterns. These include advanced persistent threats (APTs) that linger for months to years.
Threat hunting adds a proactive approach that can outsmart more sophisticated attacks, whether orchestrated by humans or AI. Experts can identify and investigate unusual behavior, resolving issues before they escalate into serious breaches. With the cost of a data breach rising each day it remains unresolved, threat hunting is key to long-term resilience.
What Are Common Challenges Faced in Threat Hunting?
Implementing and maintaining a solid threat hunting operation can come with some challenges for staffing, resources, and data volume.
A high-quality security operations center (SOC) with deep analytical knowledge is critical to effective threat hunting. However, it can be difficult for organizations to hire round-the-clock staff. Building and managing an always-on team is already time-consuming and complex, and can feel near impossible with the growing cybersecurity workforce shortage.
The sheer volume of data can also be overwhelming without the right prioritization. Improperly tuned threat hunting tools can produce a lot of false positives, leading to alert fatigue and allowing real security threats to slip past defenses. Refining powerful tools and creating complex queries that work well for threat hunting can be a long process.
Bringing in external support can turn threat hunting from a burden to a viable reality. An MDR service can augment internal cybersecurity teams with comprehensive capabilities: 24/7 security expertise and a vast security toolkit optimized for your organization.
Augment Your Security Team with Adapt MDR: The Intersection of Human Expertise and AI
Human threat hunting and AI do not have to operate as opposing forces. They can be used in tandem to improve your security posture and augment your existing team. TierPoint’s Adapt Managed Detection and Response (MDR) combines human expertise with AI-powered threat detection, monitoring your systems 24/7/365 to find hidden cyber threats and recover with minimal downtime. Discover how Adapt MDR can help your organization stay proactive and protected.

FAQs
The main types of threat hunting include structured, unstructured, and situational. Threat intelligence feeds drive structured hunts, while unstructured hunting is dependent on individual expertise, historical data, and current alerts. Situational hunting is concerned with looking at threats in specific assets or environments.
A threat hunter searches network and system data to identify and contain threats that have slipped past traditional security tools. Unlike SOC teams, which focus on monitoring, triage, and response to active alerts, threat hunters proactively investigate attacker behaviors and patterns, including alerts that may be overlooked or deprioritized during routine SOC operations. This proactive approach helps reduce the impact of vulnerabilities or malicious activity before they escalate.
Threat hunting describes the process of finding and analyzing potential threats and compromised environments. Threat intelligence refers to information feeds that cyber threat hunters can use to find out about current or emerging threats.
Threat detection relies on automated processes from security tools like intrusion detection and intrusion prevention systems (IDS/IPS). Threat hunting can be assisted by technologies but is a human-led search for threats that have not been detected by automated tools.
Threat hunting is not part of incident response (IR), but it can initiate the IR process. The vulnerabilities and security incidents found by threat hunting can equip an incident response team to isolate, remove, and remediate the environment after the threat has been discovered.
Table of Contents
-
Cybersecurity
Feb 5, 2026 | by Ed Mahoney
What Are Managed SOC Services?
VIEW MORE -
Cybersecurity
Feb 4, 2026 | by Ed Mahoney
Top Cybersecurity Trends in 2026: Rising Threats & Strategies
VIEW MORE -
Cybersecurity
Jan 22, 2026 | by Ed Mahoney
Managed Threat Hunting Explained: Benefits & Key Components
VIEW MORE
