
As businesses migrate their workloads to the cloud, more are choosing colocation. Data center demand has increased with colocation and cloud technology demand, driven by more remote workers and emerging technologies such as edge computing, artificial intelligence, and 5G networks. By the end of 2023, the colocation market is expected to reach a net worth of $61 billion, with a forecasted compound annual growth rate of 14.2% through 2030.
Of course, a move to colocation may also spark questions about security – is a move to a colocation facility a more secure option compared to hosting workloads in an on-premises data center? We’ll talk about secure colocation, the benefits businesses can enjoy with colocation services, and how migration can actually improve security.
What is Secure Colocation?
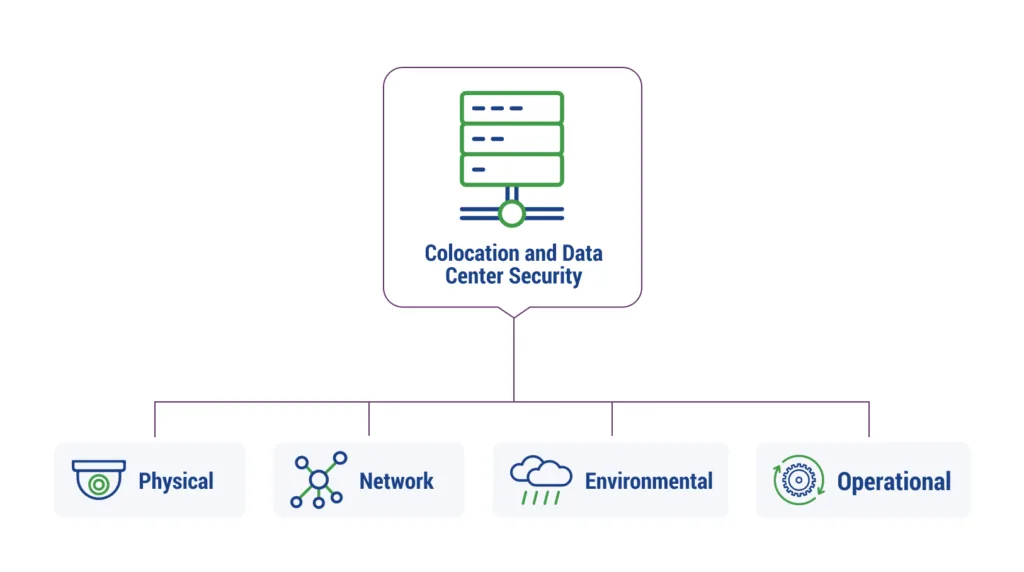
Colocation allows a business to house its IT infrastructure and equipment in a third-party data center facility. The colocation provider is responsible for various security measures at the facility, including physical, network, environmental, and operational practices. Depending on the vendor, colocation data centers may also provide managed security services, assistance with compliance, and backup and recovery solutions.
Advantages of Secure Colocation
Before you work with a colocation facility, make sure you understand the services and the features each provider offers. Most colocation data centers will come with the following security benefits.
Physical Security
Security experts often discuss the OSI’s 7-layer Network Security model, with the initial layer being the physical layer. In fact, physical data center security is one of the reasons many businesses choose colocation.
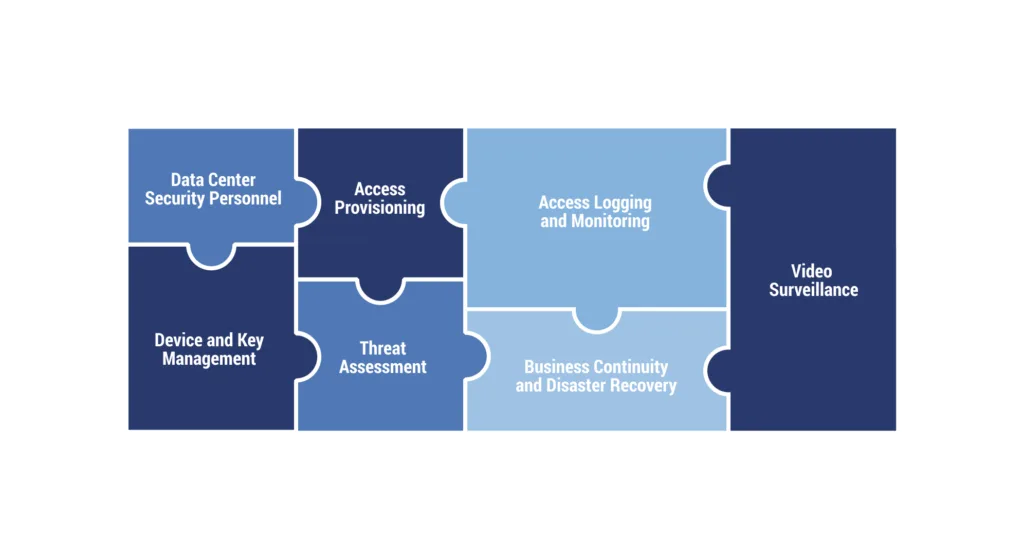
The most secure colocation data center facilities should focus on data center security, evaluation of potential threats, facilitating access, maintaining access records, consistent monitoring, ensuring business continuity and disaster recovery, managing devices and keys, and employing video surveillance.
Resiliency and Redundancy
Since you still own the infrastructure housed in a provider’s data centers, colocation doesn’t inherently address cybersecurity concerns. There are six more layers that you need to secure.
Complicating matters somewhat, cybercriminals are devising attacks that affect multiple layers. For example, a DDoS (Distributed Denial of Service) attack that starts out attacking layer 4, the transport protocol layer, might quickly switch to attacking layer 7, the application layer. Attacks can also come at you from multiple vectors, e.g., DDoS attacks are increasingly being used as a diversion while other types of attacks are launched in the background. For these reasons and more, data resiliency is essential.
If the main systems should fail, a secure colocation data center should have backups at the ready. Resiliency measures can include redundant power, cooling, and network systems, as well as a failback location for workloads to go if the main site is experiencing some kind of outage. Colocation providers that have data recovery services will have a plan in place for various disasters or attacks. When choosing a colocation provider, organizations should also keep geographical location in mind. Some areas are less prone to extreme weather than others and are therefore deemed more resilient.
Managed Services
Some colocation data centers will merely house your data and provide some base-level services, such as remote hands to execute some simple maintenance or configuration tasks. Others will offer managed services that work to protect all 7 layers.
A full-service MSP model for managed colocation means that the colocation provider manages every part of your IT infrastructure. When choosing managed services, think about the security features that are most important to your business, as well as how a provider can augment and fill in skill gaps not currently covered by your in-house staff.
Network Control
Layer 3 is the network layer, and secure colocation facilities will protect this layer by employing robust network security measures that mitigate unauthorized access or attacks including firewalls, intrusion protection systems (IPS), access controls, and virtual private networks (VPN).
How Secure Colocation Can Enhance Your Business
While colocation doesn’t offer all of the convenience and scalability of cloud computing, it does enable businesses to offload the burden of managing their facilities without squandering recent infrastructural investments. When comparing cloud versus colocation, it’s important to understand that colocation is highly beneficial for businesses with a forte in IT infrastructure, but not in facilities management. Moving to a colocation data center may also come down to wanting to route an internal team’s time to more important initiatives.
Businesses choose secure colocation facilities for a wide range of reasons. Some of the most common include:
- Existing hardware investments: If you’ve made recent investments in hardware (also known as capital expenditures), colocation can help you leverage these investments.
- In-house skills and expertise: Secure colocation allows you to refocus your IT talent. It enables you to gradually move day-to-day IT responsibilities to a managed provider. Services like smart or remote hands can free even more of your resources.
- Legacy applications: Many legacy applications aren’t architected for the cloud. Colocation allows you to manage them more closely, decreasing your exposure to cyber threats.
- Compliance & security strategy: A data center provider can offer private suites and server storage space for computing hardware. This allows businesses to manage their own infrastructure while staying secure and compliant.
- Connectivity options: Third-party data centers offer a variety of carriers and network connectivity options.
- Space restrictions: Not ready to move some of your workloads to the private or public cloud, but running out of server rooms and data center space? Renting space via colocation is an option with possible data center space cost savings.
- Physical security: On-premises data centers are incredibly vulnerable to physical man-made threats. Good colocation providers take extensive physical security precautions.
- Disaster recovery: If your business is located in a disaster-prone region, colocation allows you to house your infrastructure in a less risky area.
Making Colocation Easier
Colocation with TierPoint allows you to put your company’s IT infrastructure in our strategically located, state-of-the-art data centers. Our facilities are independently audited to ensure we have the controls, processes, and physical security features to help customers get certified as compliant with critical regulations including HIPAA/HITECH, GLBA, PCI-DSS v3.2, and ITAR. Learn about our data center locations and contact us today to request an on-site tour.

