April 26, 2024 | Channing Lovett
Understanding M365 Ransomware: Recovery & Prevention Tips

Any business of any size can be vulnerable to attacks, particularly ransomware. In 2023, ransomware accounted for one-quarter of all malicious attacks. One of the reasons ransomware has been on the rise can be attributed to the growing popularity of ransomware as a service (RaaS), making it easier than ever for cybercriminals with less sophisticated skills to commit ransomware attacks.
Why M365 is a Ransomware Target
Microsoft 365’s large userbase makes it a particularly attractive target for cybercriminals. Small businesses and large enterprises alike can use M365, so if a vulnerability is found in the system, bad actors can exploit it to gain access to a larger user base compared to less popular platforms.
While M365’s interconnected environment is convenient for businesses, it can pose a greater risk during a ransomware attack, making the spread of encryption or theft easier.
Compromised endpoints, such as unpatched software vulnerabilities and access via malware, are popular points of entry for ransomware attackers, but they can also use other ways to gain access to systems. In June 2023, a company experienced a ransomware attack against their Sharepoint Online environment that was carried out by a cybercriminal using a Microsoft Global SaaS admin account.
Common Ransomware Attack Vectors
Tactics used by ransomware criminals are constantly changing, but some of the most common attack vectors include:
- Phishing emails: Criminals send emails posing as legitimate sources, asking for key information or tricking recipients into clicking malicious links.
- Supply chain attacks: Sometimes, the problem doesn’t start with your business. It starts with a third-party vendor that has been compromised, leading to an attack on your business systems later on.
- Software vulnerability exploitation: M365 unpatched vulnerabilities, especially in their initial stages (zero-day), can serve as a great backdoor for ransomware.
- Compromised credentials: Malware, weak passwords, and phishing emails can help cybercriminals gain access to user credentials, allowing them a way to further infiltrate systems.
- Unsecured remote desktop protocols (RDP): Organizations that use remote access for maintenance or to allow more flexibility for remote workers can be more vulnerable to attacks if the correct configurations are not in place.
The Business Impacts of M365 Ransomware
How M365 ransomware impacts businesses will depend greatly on how much the organization relies on M365 for their critical operations, as well as how many safeguards against ransomware are already in place. For companies that don’t have a plan to recover from ransomware, especially those without backup and data recovery strategies, the fallout from ransomware can be catastrophic.
Disruption of Operations
Because businesses can store so much in their M365 environments, experiencing data inaccessibility as a result of a ransomware attack can bring operations to a grinding halt. Organizations may experience operational paralysis, finding themselves unable to make key decisions that move the business forward, because their files are inaccessible.
Financial Losses
M365 ransomware attacks can inflict a crippling financial blow on businesses. The most immediate hit comes from the ransom itself, which can range from a few thousand to millions of dollars. But the financial losses extend far beyond that initial demand. Negotiations with attackers can drag on, incurring legal or professional fees, and forensic investigations to understand the attack and identify vulnerabilities are expensive endeavors.
Other notable financial losses typically include associated downtime costs, data loss or theft expenses, remediation costs, reputation damage, regulatory fines, additional legal fees, and lost revenue.
Loss of Trust
Data breaches don’t just hurt your finances, they can also permanently harm brand reputations. A business that has experienced a ransomware attack can receive negative publicity. An iffy reputation can also hurt future business opportunities, well after the fallout from an attack has subsided.
Legal and Regulatory Compliance Problems
Some industries require certain safeguards against ransomware. The consequences of ransomware can include legal fines or other regulatory penalties, making compliance crucial for organizations and non-compliance can also render cyber insurance invalid, resulting in greater financial losses.
How to Prevent a M365 Ransomware Attack
Microsoft 365 operates on a shared responsibility model. While Microsoft is responsible for the infrastructure and underlying system, businesses using it are accountable for protecting their data. This means that preventing a ransomware attack on M365 data requires implementing additional security measures and offering end user training to recognize common threats.
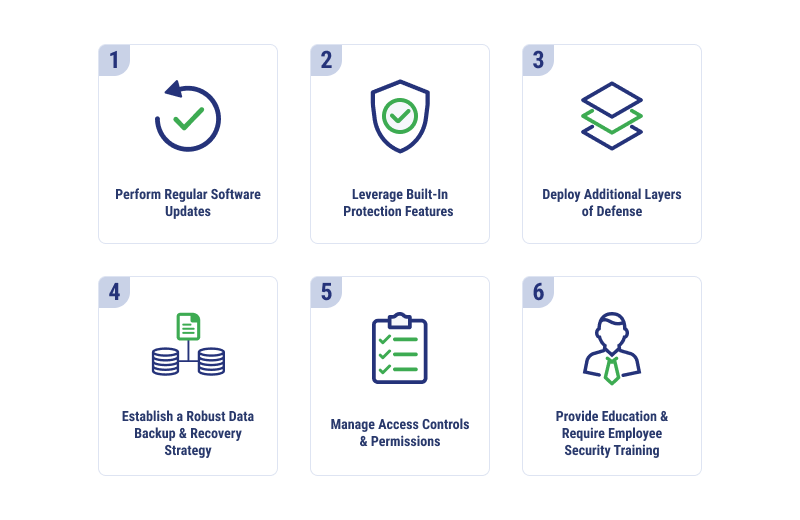
Perform Regular Software Updates
One of the most important steps a business can take in protecting against ransomware is also one of the simplest. When M365 systems have software updates, it’s important to apply them as soon as possible. While some updates may be related to functionality, many have to do with patching newly discovered vulnerabilities.
According to IBM’s Cost of a Data Breach report, approximately 17% of data breaches come from either known, unpatched vulnerabilities (6%) or zero-day vulnerabilities (11%). This means it’s important to stay up-to-date on the most recent threats, as well as not let much time pass before making updates on known issues. Consider implementing automatic updates and scheduling regular patch days for your organization.
Leverage Built-In Protection Features
Microsoft 365 has several built-in security measures that can reduce the threat of ransomware. These tools include Microsoft Defender, Safe Attachments, and Multi-Factor Authentication (MFA). While these tools are not all a business should be using to defend against ransomware, they can serve as a strong first line of defense.
Deploy Additional Layers of Defense
In addition to implementing MFA and other tools native to M365, organizations should consider adding specialized solutions or tools to their ransomware protection plan. For example, data protection is still the responsibility of the business, so managing encryption, protecting sensitive data, and configuring tools to prevent data loss are all tasks for the business to take on.
Establish a Robust Data Backup and Recovery Strategy
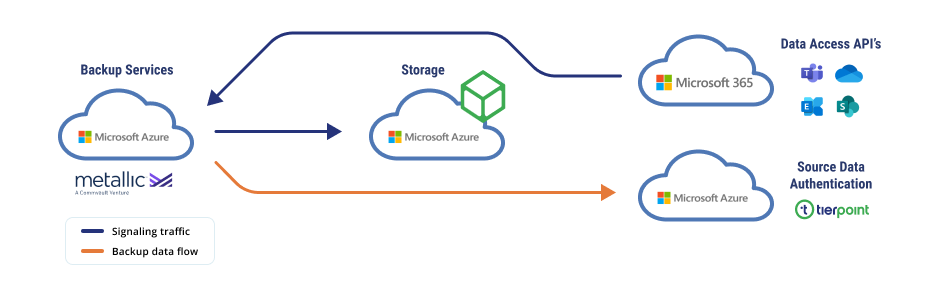
One of the tools that may be included as an additional safeguarding layer could be part of a larger data backup and recovery strategy. Backup services and tools can help a business recover from ransomware attacks by providing a geographically distinct site for data that cybercriminals may encrypt. TierPoint’s M365 backup services, for example, allow for automated backups, improved data availability, data protection from ransomware, as well as the implementation of air gapping and immutable backups.
Manage Access Controls and Permissions
There’s no organization where every user requires the same level of access. Different departments, organizational levels, and skill sets will require different access points in a M365 environment. Manage permissions and access controls based on what different segments and individual team members are likely to use in your business. You can always change permissions temporarily for special projects. Plan time to regularly review permissions and make changes as necessary.
Provide Education and Require Employee Security Training
Employees can be a significant source of ransomware attacks, from falling victim to phishing emails and social engineering, to lost credentials, to other business email compromises, employees account for a significant amount of data breaches and malicious attacks. Train employees on best practices to avoid ransomware to decrease the risk from these attack vectors. You can even further test them periodically using fake phishing emails and other simulated drills.
Data Recovery Options
In general, businesses have one of two options for data recovery – logical or physical. When there’s something wrong with the physical form of storage itself, physical data recovery is needed to replace damaged parts. However, ransomware is most concerned with logical data recovery, which involves using data backups, data recovery software, or professional data recovery services to regain access to lost or locked data. TierPoint’s disaster recovery as a service (DRaaS) offerings can help organizations meet their recovery time objectives (RTO) and recovery point objectives (RPO), while restoring access to data through cloud-by-cloud recovery. Other businesses may benefit from backup as a service (BaaS).
How Can You Recover from an M365 Ransomware Attack?
Unfortunately, some businesses start thinking about ransomware attacks only after they’ve experienced one. To begin ransomware remediation and recover from an M365 attack, you need to immediately isolate the infected systems to stop the spread. Then assess network vulnerabilities and prioritize the recovery of critical data and systems to maintain business operations.
However, prevention is truly the best form of protection to avoid a ransomware attack. Managed service providers can assist in crafting and implementing these preventative measures and recovery strategies emphasizing the importance of preparation.
Safeguarding Your M365 Environment Against Ransomware Threats
Successfully safeguarding your M365 environment from ransomware threats requires a multifaceted approach. By employing Microsoft’s tools, bringing in additional resources, and regularly training your staff, you can fortify your M365 environment against attacks. TierPoint’s IT Disaster Recovery Services include Backup and Recovery for Microsoft 365 Powered by Metallic, as well as complementary solutions that can make your environment much less vulnerable. Download our eBook to explore the comprehensive benefits of implementing a M365 data backup and recovery plan.

