
Table of Contents
Whether you’re shifting from one cloud to another or moving out of your on-premises environment, cloud migration projects can be beneficial to your organization in many ways. With the right public cloud provider—such as AWS, Azure, or Google Cloud—companies can optimize their IT spend, performance, and flexibility all at once.
Cloud platforms can offer robust security features, too. However, keep in mind that neither on-premises nor cloud environments are immune to vulnerabilities. Plus, migrating to the cloud doesn’t mean that cybersecurity becomes the cloud provider’s sole responsibility. That’s why enhancing security measures is the No. 1 priority for IT leaders, according to TierPoint’s 2025 Technology & IT Modernization Report.
Understanding key cloud migration security risks is an important part of keeping your organization safe during and after your transition. We’ll cover some key steps to ensure safety in the cloud.
What Is Cloud Migration Security?
Cloud migration security refers to the combination of strategies, practices, and controls used to ensure infrastructure, applications, and data are protected, either when moving from one cloud to another or migrating from on-prem to cloud. Considering cloud migration security is important for organizations looking to protect their data at rest and in transit, safeguard against new attack vectors, address their duties in a shared responsibility model, and maintain regulatory compliance.
Cloud Security vs. On-Premises Security
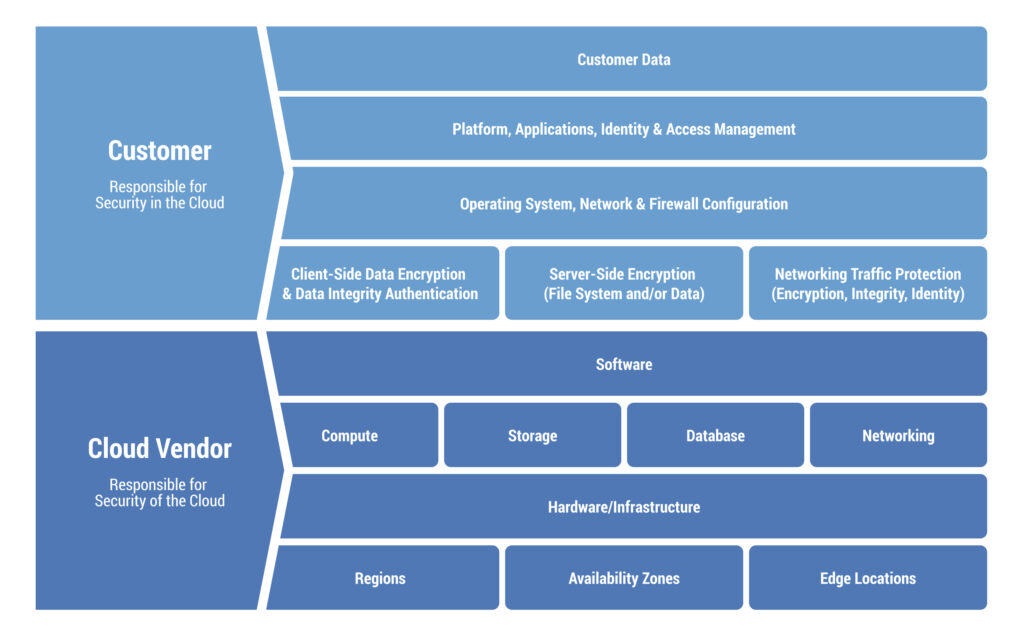
When businesses host their data and applications in an on-premises environment, they maintain full control over their security infrastructure. They may even have customized security solutions in place for the processing and storage of data and applications. Staying on-prem allows organizations to manage every aspect of workload security, including physical data center protection, server patching, network firewalls, data protection, and application security. However, this high level of control comes with high costs and responsibilities.
Conversely, cloud security requires cloud service providers and their clients to be mutually responsible for the security of their systems. Providers take care of physical and network infrastructure security. Additionally, many offer optional advanced services, such as intrusion detection and prevention systems (IDS/IPS), web application firewalls (WAF), DDoS protection, and threat intelligence feeds that organizations can purchase.
However, organizations hold much of the responsibility for protecting their applications and data housed in the cloud and during migration. This involves managing cloud service and security configurations, data encryption, access controls, and compliance requirements.
What Are Common Cloud Migration Security Risks?
Migrating to the cloud comes with many benefits, but it also introduces new security risks. As you make your transition, you’ll want to be mindful of these risk areas and common mitigation strategies.
Data Loss and Leakage
Data loss can often happen as a result of inadequate encryption, unsecured storage buckets, and poor data classification prior to migration. These lax controls can leave data susceptible to loss or theft. Organizations can mitigate these risks by implementing end-to-end encryption, tagging, and proper data classification, and ensuring all cloud storage buckets are configured for private access.
Misconfigurations
Misconfigurations are commonly caused by issues such as:
- Failure to change default settings in cloud computing services
- Insufficient automation that leads to more frequent human errors
- Poor visibility in cloud resource configurations, which makes it harder to spot errors
These problems can be addressed by automating configuration management, deploying cloud security posture management (CSPM) tools that monitor for misconfiguration, and conducting regular audits of cloud configurations.
Regulatory Compliance Issues
Your organization will face specific regulatory requirements based on your industry, the data you collect, and your location. However, when migrating to or operating in a new cloud environment, some compliance obligations may look slightly different. Businesses must understand their obligations for compliance under the shared responsibility model and should conduct a cloud compliance assessment before choosing to work with a particular cloud provider. Depending on what is already offered, IT teams may need to implement additional policies and automated compliance tools to monitor their status in a cloud environment.
Identity and Access Management (IAM) Lapses
The access your users need in one moment may change in the next. However, without regular reviews, team members may be over-privileged, leading to unnecessary access and additional sources of vulnerability. Other identity and access management (IAM) lapses can stem from weak authentication, a lack of centralized IAM systems, and insufficient credential management.
Businesses can keep access in check and avoid unnecessary permissions by:
- Implementing a centralized IAM solution
- Routinely reviewing access
- Enforcing multifactor authentication
- Executing the principle of least privilege (POLP)
Human Error & Insider Threats
Sometimes, the issues can simply come from human error, particularly if employees aren’t familiar with the best practices of cloud security. Less commonly, malicious insiders can exploit their access to steal data or harm the system in another way. All employees should receive comprehensive training, and security teams should set up automated guardrails that identify common human errors or anomalous activity. Logging and monitoring can help you spot potentially malicious behavior, and abiding by the aforementioned principle of least privilege can limit the access any malicious insiders would have to your processes.
API Vulnerabilities
APIs can be developed with unsecure designs, broken authentication and authorization processes, and misconfigured gateways. If APIs haven’t been set up with rate limiting in place, they can also be susceptible to brute-force or cloud malware like denial-of-service (DOS) attacks. All APIs should be designed with security principles in mind, including strong authentication and authorization practices. API gateways can monitor and secure API traffic, forcing rate limiting, authentication, and authorization. Regular vulnerability and penetration testing can also help highlight vulnerabilities before they get worse.
Vendor Risks
When third-party vendors have access to your cloud environment, they bring with them additional security risks. As part of the shared responsibility model, organizations need to think about vetting the security practices of third-party vendors and anyone in their software or physical supply chain. Performing thorough due diligence, establishing contractual agreements, and monitoring third-party access can help cut down on vendor risks.
Key Elements of Cloud Migration Security
A successful cloud migration strategy thoroughly evaluates risks and implements continuous processes that integrate security at every stage.
Risk Assessment and Management
Before migration, conduct a thorough risk assessment to identify potential security risks and vulnerabilities. Create a migration plan that includes security considerations to mitigate these risks effectively. Knowing what data is being migrated and what potential vulnerabilities are possible can help you create approaches that counter any threats.
Configuration Management
Ensure that cloud resources are configured securely. Follow best practices and guidelines provided by the cloud provider to avoid misconfigurations that can lead to vulnerabilities. This can include setting up secure baseline configurations for cloud services, automating infrastructure and configurations using infrastructure as code (IaC), and implementing monitoring tools to keep tabs on cloud configurations.
In addition to secure baseline configurations, ensure network segmentation using virtual private clouds (VPCs), private subnets, and firewall rules. Limit public IP exposure by using private endpoints or service endpoints, and apply web application firewalls (WAF) or DDoS protection services to shield internet-facing applications.
CI/CD Pipeline Security
Secure migration also extends to your CI/CD pipeline. Protect pipelines by scanning IaC templates for misconfigurations, securing credentials in secret management systems, and using image/container scanning if migrating containerized workloads.
Integrating security checks early in the software development lifecycle, an approach known as shift-left security, helps catch vulnerabilities before deployment.
Compliance and Regulatory Considerations
Major cloud providers are compliant, or can be compliant, with major regulatory standards like HIPAA and the General Data Protection Regulation (GDPR). However, some additional features or configurations may need to be added for environments to be considered compliant. Organizations should understand regulatory requirements in the cloud and the changes that may need to be implemented when moving from an on-premises environment.
Data Protection and Privacy Measures
Data protection and privacy throughout the cloud migration lifecycle can be supported through data encryption and identity and access management (IAM).
Data Encryption
When an organization’s data is encrypted, unauthorized users can’t read it because it’s scrambled, even if a data breach occurs. Secure data should be encrypted both at rest and in transit. This could be done at rest with services such as AWS Key Management Service (KMS) or Azure Key Vault, as well as client-side encryption. In transit, use a strong protocol such as (Transport Layer Security (TLS) or Secure Sockets Layer (SSL).
For highly sensitive data and workloads, organizations may choose Bring Your Own Key (BYOK) models or dedicated Hardware Security Modules (HSMs) to maintain additional control over encryption keys.
Identity and Access Management
Not every user needs the same level of access. Some users may need administrative access to certain environments, whereas others won’t need authorization at all. Understanding necessary levels of access and doling them out appropriately can limit the risk that comes from application and data access.
Backup and Disaster Recovery
Implement robust backup and disaster recovery strategies to ensure business continuity in case of data loss or service disruption. Backups should be immutable to prevent ransomware from encrypting or deleting files, and automated backup solutions can help organizations meet their RPOs and RTOs.
Cloud-native backup solutions such as AWS Backup or Azure Backup can integrate with cloud resources and support policy-based backup automation, cross-region replication, and ransomware protection.
Ongoing Monitoring and Incident Response
If a security incident happens, a plan should already be in place for how to respond. How will incidents be found, contained, and addressed? Be sure to implement continuous monitoring so security threats can be detected and handled quickly. Centralized logging and monitoring through a Security Information and Event Management (SIEM) system and with a cloud-logging service (Amazon CloudWatch, Google Cloud Logging, Azure Monitor) can serve as a robust integrated program for improving visibility in your cloud environment.
Types of Cloud Migration: Top Security Considerations
The right approach to cloud migration for your organization will depend on your security capabilities and specific needs. See the seven Rs of cloud migration below for basic definitions and common security challenges.
| Migration Strategy | Description | Key Security Challenges |
| Rehosting (Lift and Shift) | Making minimal changes to applications and data to move them to the cloud |
|
| Refactoring | Performing small, incremental code optimizations to applications to harness cloud-based features, without changing code functionality |
|
| Replatforming | Making modifications, such as exchanging components for cloud equivalents, without rearchitecting the code |
|
| Repurchasing | Removing the previous application and replacing it with a new purchase, generally a SaaS solution |
|
| Retaining | Keeping applications and data in the original environment, rather than switching to compatible alternatives |
|
| Retiring | Removing applications and data that are no longer necessary |
|
| Rebuilding | Fully rewriting the code of applications to leverage cloud-native services |
|
Best Practices to Mitigate Cloud Migration Security Risks
Many cloud migration challenges, including security risks, can be significantly reduced by periodically revisiting access controls, organizational responsibilities, business-wide safeguards, and more. To summarize some of what we’ve discussed, we’ve compiled some best practices for mitigating potential risks from cloud security.
Access Control
Implement the principle of least privilege to limit access to only what is necessary for each user’s role. Downgrade or decommission access when it’s no longer needed.
Automation
Automating processes can cut down on manual errors. Any steps in cloud migration and management that are repetitive may be able to be handled by an automated ruleset.
Visibility
The more you gain visibility over your cloud environment, the more you’ll be able to identify suspicious behaviors and protect your systems from cybersecurity attacks. Some security tools can present data from multiple cloud environments, but make sure whatever you use has a comprehensive view of your entire IT landscape.
Responsibility
It’s the responsibility of the organization to protect its data and applications, but roles within the organization can vary. Whether you’re working with outside cybersecurity experts or not, you’ll want to assign responsibilities for configuring security controls, monitoring, responding to security incidents, educating employees, and communicating with internal and external stakeholders.
While implementing robust security, balance cost savings and performance impacts. Evaluate when to use reserved or spot instances for disaster recovery, when to enable premium security services, and how third-party tools integrate with native controls to avoid redundant spending.
Multi-Factor Authentication (MFA)
Multi-factor authentication requires all users to provide more than one source of authentication for logins. For example, a user may log in using a name and password but will also be required to verify their identity using an app on their phone or by inserting a physical key.
Today, MFA is required by 83% of organizations for IT resources, and the technology industry is on the leading edge of MFA implementation with 87% adoption rates. Requiring MFA can substantially reduce the risk of unauthorized logins.
Make Cloud Migration Security a Priority with TierPoint
Taking on a cloud migration project is stressful enough. Security shouldn’t be a worry added to your list. Working with experts who are skilled in both cloud migration and cybersecurity can keep you focused on cloud innovation instead of looking over your shoulder, worried that you forgot about a key vulnerability.
Whether you want to assess your cloud readiness, move legacy apps, or strengthen your cloud migration security strategy, TierPoint has services and solutions to help. Learn more about the skills you need before starting a cloud migration.

Table of Contents
-
Artificial Intelligence (AI)
Feb 11, 2026 | by Mikael Grondahl
Top Trends for AI in Data Management in 2026
VIEW MORE -
Cloud
Jan 19, 2026 | by Matt Pacheco
IT Trends Report: Hybrid, AI, and Security Investments Accelerate Through 2030
VIEW MORE -
Cloud
Jan 8, 2026 | by Matt Pacheco
What Is Cloud TCO? How to Calculate Total Cost of Ownership
VIEW MORE
