Published: January 21, 2026 | Last Updated: January 26, 2026
IPS vs. IDS in Cybersecurity: Creating a Layered Defense

Table of Contents
In today’s cyber threat landscape, security leaders aren’t debating whether to detect or prevent attacks. They’re focused on how quickly detection can be operationalized into reliable, automated prevention. As threat volumes grow and time-to-impact shrinks, security teams need controls that evolve from visibility to enforcement without introducing unnecessary risk or disruption.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) have long played foundational roles in network security. But in modern environments, they are no longer viewed as standalone or competing technologies. Instead, they represent a progression within a single control lifecycle, from observing and tuning detections to confidently enabling inline prevention.
Understanding IDS and IPS through this lens helps you design layered defenses that reflect how these tools are actually deployed today: IDS as the validation and tuning phase, and IPS as the enforcement engine that follows.
What Is an Intrusion Detection System (IDS)?
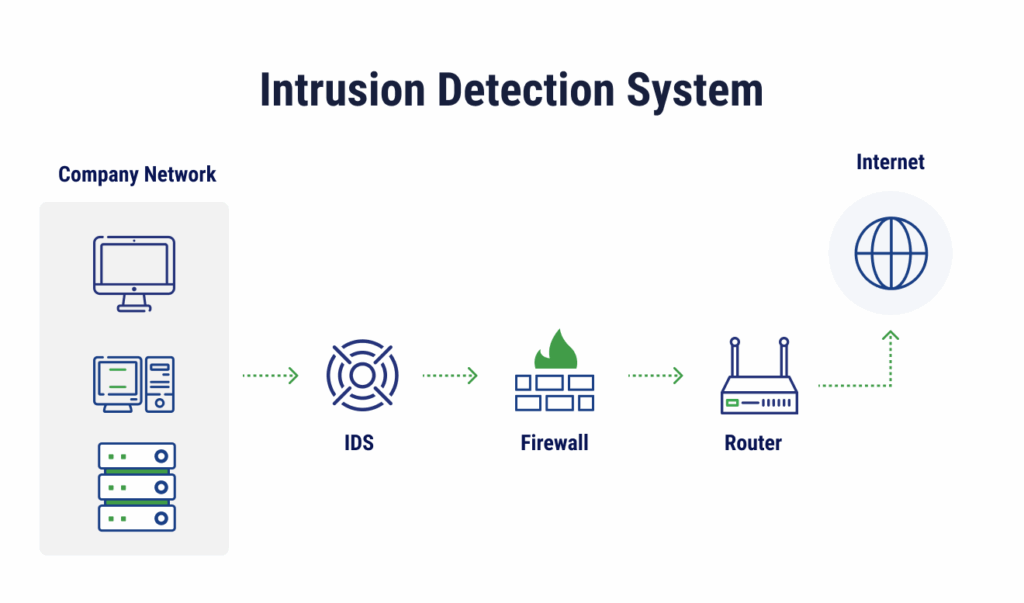
An intrusion detection system (IDS) monitors a network or system to identify suspicious behavior, policy violations, or known malicious patterns. When it detects a potential threat, the IDS generates alerts for security teams to review and investigate.
IDS is a passive system that doesn’t take action on its own. IDS started as a signature-based alert tool but now serves mainly as a visibility and testing layer. Security teams use it to monitor traffic, verify detections, and fine-tune rules before turning on active blocking. It’s not the final goal but a safe first step to see how detection logic works in real conditions before moving to prevention.
How Does an IDS Work?
An IDS uses both signatures and behavioral baselines to analyze traffic and logs. Signature-based detection identifies known malicious activity, while baseline‑driven anomaly detection identifies activity that deviates from expected behavioral or policy patterns. This makes IDS especially valuable during:
- Initial deployment of detection rules
- Validation of new signatures or policies
- Threat hunting and forensic investigations
What Are the Main Types of IDS?
IDS capabilities can be deployed at different control points depending on where visibility is required. The two most common approaches, network-based and host-based IDS, are often used together to provide comprehensive detection coverage across modern environments.
Network-Based Intrusion Detection System (NIDS)
NIDS solutions are placed at specific points in the network, such as behind the firewall or near sensitive assets, to monitor and analyze traffic passing through a subnet. They typically inspect a mirrored copy of network traffic, usually via a network Test Access Point (TAP), which prevents disruptions in network performance.
Host-Based Intrusion Detection System (HIDS)
A HIDS is placed at individual endpoints, which can include laptops, workstations, and servers. These systems look at the internal activity of devices, such as process activity, application logs, file system changes, and system calls. This can help detect security threats that have already made it past the network perimeter.
Benefits of Using an IDS
While IDS alone is rarely considered sufficient protection, it remains valuable for:
- Observing traffic safely without blocking legitimate activity
- Reducing risk during early deployment or rule tuning
- Providing context that supports threat hunting, forensic investigations, and incident response measures
- Meeting logging and auditing requirements for regulatory compliance
What Is an Intrusion Protection System (IPS)?
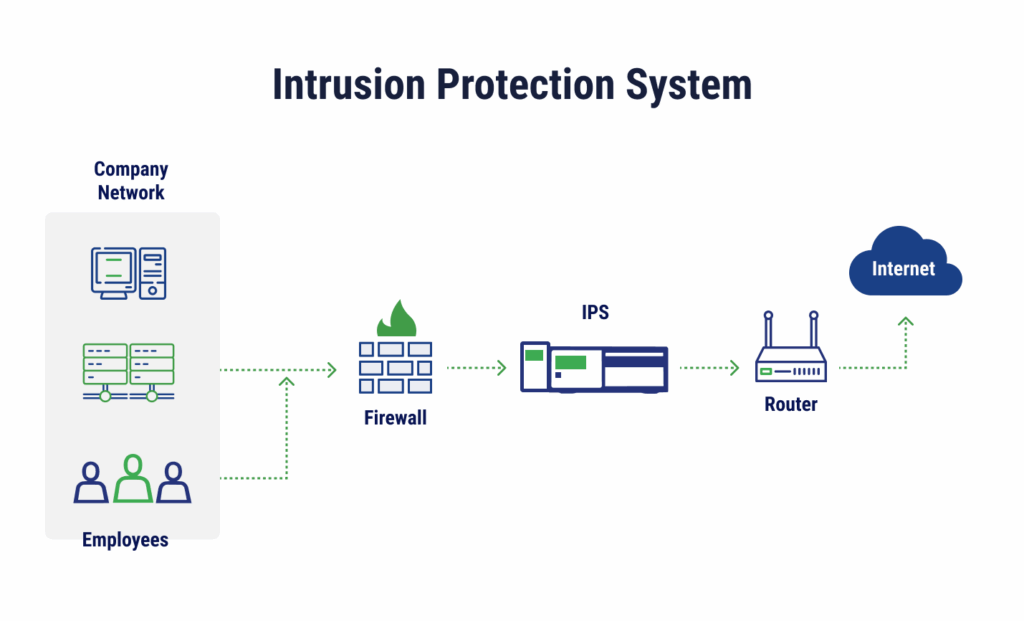
Intrusion protection systems (IPS) build upon IDS capabilities with automated responses that prevent malicious activity. These tools sit inline with network traffic and can analyze, intercept, and block malicious activity in real time.
In modern environments, IPS is typically enabled after IDS detections have been validated, allowing organizations to shift from alerting to real-time enforcement with reduced risk of false positives.
How Does an IPS Work?
An IPS uses similar detection methods to an IDS, but uniquely operates inline with network traffic. When malicious activity is detected, the IPS can respond with proactive security measures like blocking future traffic, resetting connections, reconfiguring firewalls, and dropping malicious packets. This enables immediate mitigation without waiting for human intervention.
What Are the Main Types of IPS?
IPS solutions can focus on protecting specific endpoints, or they can secure the broader network in various ways.
Network-Based Intrusion Prevention System (NIPS)
The most common type of IPS is the network-based IPS. This solution inspects packets in real time as they move across the network, blocking malicious traffic before it reaches its destination.
Host-Based Intrusion Prevention System (HIPS)
A HIPS focuses on analyzing activity on individual machines, defending against registry changes, unauthorized application actions, and file modifications. These can help capture threats that get past network security measures.
Wireless Intrusion Prevention System (WIPS)
Cyber threats can also attack an organization’s wireless network. A WIPS can scan the radio frequency spectrum to detect attacks on the wireless network with unauthorized devices or via rogue access points
Benefits of Using an IPS
When properly tuned, IPS delivers:
- Real-time threat prevention
- Reduced mean time to response (MTTR)
- Less alert fatigue for security teams
- Stronger enforcement of security and compliance policies
Types of IDS and IPS Detection Methods
Detection methods for IPS and IDS tend to be based on signatures, anomalies, or policies.
Signature-Based Detection
Signature-based detection looks for predetermined patterns related to known attacks and flags them for future action. IDS tools will trigger alerts based on signatures associated with known exploits, attack techniques, and malware. IPS tools will drop the traffic that is affiliated with these signatures. While this detection method can be very accurate, it isn’t effective against zero-day attacks.
Anomaly-Based Detection
Anomaly-based detection uses “normal” behavior to flag anything that is abnormal. The system starts by learning what expected behavior looks like–for example, when users normally log in, the average sizes of system files, or what bandwidth consumption typically is. When something falls outside the baseline, IDS systems will trigger a warning, while an IPS tool can block or mitigate the traffic causing the anomaly.
Policy-Based Detection
Policy-based detection monitors whether activity on the network or system abides by established security policies and rules. When there is a violation of security best practices or regulatory guidelines, the IDS system can issue an alert, and the IPS system can prevent traffic that is causing the violation.
What Are the Main Differences Between an IDS and IPS?
IDS and IPS are no longer standalone solutions. They now function as a single progression within a broader security platform. When we look at the different roles they play, the importance of implementing both for a layered security approach becomes clear.
| Technology | IDS | IPS |
| Primary Role | Detection and tuning | Prevention and enforcement |
| Deployment | Out-of-band | Inline with traffic flow |
| Traffic Impact | Minimal | Potential latency if misconfigured |
| Response | Alerts security teams | Blocks traffic based on automatic rulesets. Can also change policies or reset connections. |
| Typical Use Today | Observation and validation | Full production protection |
Detection vs. Prevention
The main difference between IDS and IPS is the role each plays in detection versus prevention. IDS operates like an alarm, allowing alerts and tuning to occur. In response, IPS acts like a bouncer, taking immediate action to block and mitigate damage from an attack for full prevention.
Can IPS and IDS Work Together?
IPS and IDS can work together, and in modern environments, they usually do.
Most modern security platforms, including next-generation firewalls (NGFWs), integrate IDS and IPS into a single, unified solution. Teams can run in detection-only mode initially, then transition seamlessly to inline prevention once confident in their policies.
This reflects how IDS and IPS are actually used today: not as competing tools, but as phases of the same control within a modern security architecture.
Leverage a Unified Security Platform Powered by AI and Human Expertise
A unified security platform can further enhance an organization’s defenses by combining an NGFW with endpoint protection, antivirus, managed detection and response (MDR), and more security capabilities. Businesses can reap the benefits of AI-powered automations, reducing false positives and cutting down on alert fatigue, all while accessing human expertise.
Designed for how security teams actually operate today, the TierPoint Adapt Platform supports the full IDS-to-IPS lifecycle, combining AI-driven detection with human-led response to deliver visibility, validate threats, and enable rapid action across hybrid and multicloud environments.

FAQs
A network intrusion is any unauthorized activity that may happen on a network that can compromise security. Some motivations for network intrusions can include gaining access to certain information, stealing data, or damaging the network in some way.
Intrusion detection systems (IDS) will monitor the network and will send alerts for malicious activity, but they cannot block anything. Intrusion prevention systems (IPS) will detect threats and block network traffic in real time. Data loss prevention (DLP) systems are mostly concerned with sensitive data, particularly preventing it from being leaked or shared beyond the network.
Firewalls control network traffic by allowing or blocking connections based on predefined security rules. Modern next-generation firewalls (NGFWs) often combine traditional firewall functions with intrusion detection (IDS) and intrusion prevention (IPS) capabilities in a single platform.
IDS and IPS go beyond simple access control to analyze traffic for signs of malicious activity. IDS focuses on detecting and alerting on potential threats, while IPS operates inline to automatically block or stop those threats once detection rules have been verified and tuned.
Yes. IDS and IPS capabilities are commonly integrated with broader security ecosystems, including SIEM platforms, NGFWs, and managed detection and response (MDR) services. This integration enables centralized visibility, coordinated response, and a seamless transition from detection to enforcement within a layered security architecture.
Table of Contents
-
Cybersecurity
Feb 5, 2026 | by Ed Mahoney
What Are Managed SOC Services?
VIEW MORE -
Cybersecurity
Feb 4, 2026 | by Ed Mahoney
Top Cybersecurity Trends in 2026: Rising Threats & Strategies
VIEW MORE -
Cybersecurity
Jan 22, 2026 | by Ed Mahoney
Managed Threat Hunting Explained: Benefits & Key Components
VIEW MORE
