June 13, 2023 | Channing Lovett
How to Create a Proactive Vulnerability Management Framework

Whether you’re aware of your vulnerabilities or are not, hackers are. They’re watching reports of vulnerabilities to exploit, banking on the fact that most organizations will not act swiftly, or at all, to remediate weaknesses. No matter your size, industry, or systems, having a vulnerability management framework in place is your best line of defense against these bad actors.
What is a Vulnerability Management Framework?
A vulnerability management framework, also known as a vulnerability management strategy, is all about how you assess and protect against risks or vulnerabilities in your environment. Even though every network is vulnerable to attack, not every network shares the same vulnerabilities.
Deployed systems, processes, applications, industry, and organizational culture are all parts of your unique IT security risk profile. This is why understanding the vulnerability management framework and how it applies to your business is so crucial.
Organizations need to identify all risks both internal and external that can adversely affect the organization with a strategy to manage and mitigate those identified risks.
Four Stages of Vulnerability Management Framework
The vulnerability management framework includes four key stages – identification, evaluation, treatment, and remediation.
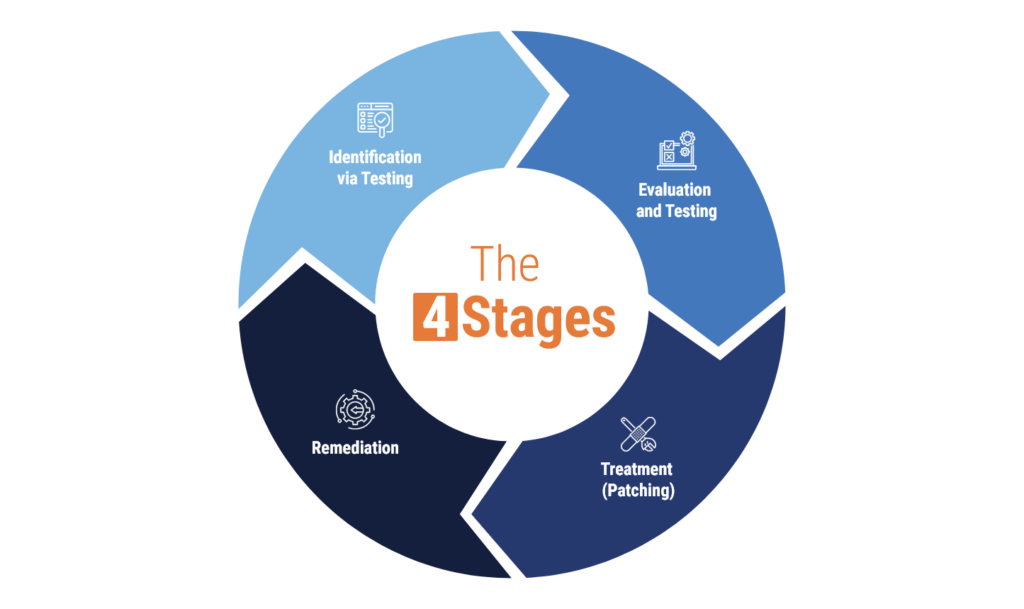
Identification via Testing
Understanding your risks starts with an in-depth Security Assessment leveraging vulnerability scanning and penetration testing to find risks and weaknesses in your existing security approach.
A vulnerability scan is performed using a specialized software application that inventories all of the systems on your network and looks for vulnerabilities that can be exploited by hackers.
It’s essential to run scans periodically as known threats change rapidly. Advanced vulnerability threat scanning applications incorporate threat feed analysis from major OS developers, regulatory agencies, and other sources, sometimes updating scanning algorithms as frequently as twice per day.
Some key industry regulations require scans to be run at specified intervals – not necessarily twice a day, but there are standards. For example, PCI DSS requires a vulnerability scan every 90 days. As a best practice, TierPoint runs scans against our infrastructure every 30 days, unless the announcement of a critical vulnerability triggers an ad hoc scan of either a specific component or the entire network.
Evaluation and Testing
While a vulnerability scan can help you identify how to protect your systems, it doesn’t actually protect them. Critical flaws need to be identified and prioritized next – this can be done through evaluation and penetration testing.
The vulnerability scans TierPoint conducts give us a baseline for how well our clients are secured against known threats. We then take the results of the scan and highlight all the critical flaws, i.e., those that are easily exploited by hackers, including those that aren’t highly skilled. There’s a good reason for this. By the time a critical flaw shows up, there’s probably a threat analysis posted on the dark web, with step-by-step instructions showing non-skilled hackers how they can exploit a known vulnerability to gain access to their targeted victim’s systems.
After we run a routine vulnerability scan, we pick the top ten vulnerable components and run a penetration test. Using available tools, we try to exploit our infrastructure to see how vulnerable we are to critical threats.
By helping us identify which components are most open to being hacked, vulnerability scans allow us to focus our efforts when dealing with a large infrastructure like TierPoint’s.
From there, you can take action with patch management.
Treatment (Patching)
Hardware, operating systems, and applications are all components that need periodic patching regardless of which vendor created them. Patches are often written to improve the functionality, security, usability, or performance of a program or operating system. A vulnerability scan and follow-up penetration test can help you identify patches that need to be applied immediately.
Traditionally, many IT leaders have been somewhat wary of applying patches as soon as they are released because their neck is on the line if an application becomes unusable. Vendors can’t possibly test their patches against every commercial application before they release them. It wouldn’t even be worth attempting as the same application can have different vulnerabilities based on how it is configured. So, these IT leaders wait, hoping someone else will uncover any issues before they apply the patch.
When a manufacturer releases a patch, they usually give pretty explicit details on the vulnerabilities being addressed. IT leaders can use this information to assess any potential issues before applying the patch. Unfortunately, hackers will also use this information to identify which vulnerabilities to exploit.
Remediation
Patch management can solve many problems, but it may not be able to address all issues that arise. If your production environment needs to be configured in a certain way for an application to run, you may not be able to fix a vulnerability. However, you can still lessen the threat by creating a perimeter of security around your network using a variety of threat detection and remediation tools.
Remediation may include tools such as web application firewalls (WAFs), next-gen firewalls, and log management tools. It would also include best practices in areas such as password management, especially of edge devices, and credentials management.
What to Include in Your Vulnerability Management Framework Policies and Procedures
A plan is only worth something if it’s carried out. A vulnerability management program requires solid policies and procedures to ensure nothing gets missed amidst the other distractions of daily operations.
Vulnerability Management Policy
First, an organization should design a vulnerability management policy that outlines how each of the above pieces of the framework will be carried out. This policy should detail:
- How often vulnerability scans will be conducted
- How vulnerabilities will be prioritized
- How patch management will run
- How changes in vulnerabilities and patches will be documented and reported
- What remediation measures should be considered for each vulnerability
The policy should also include language on how often it will be reviewed and potentially revised as vulnerability management evolves in the organization.
Risk Assessment Procedure
Similar to vulnerability assessment, there should also be a procedure for assessing risks. Vulnerabilities are generally seen as internal processes and weaknesses that can be exploited by bad actors, whereas risks are associated with outside risks. How you determine which outside events will affect your business will be part of your risk assessment procedure.
Patch Management Procedure
How will you decide to patch your systems – how often, what steps will your security team follow, and so on? For most components, TierPoint maintains a 30-day rolling patching window. This means that we don’t patch everything at once, but we do apply patches at least every 30 days. How you conduct your patching schedule and order of operations should be included in your procedures.
Incident Response Procedure
When a security incident occurs, what will your organization do to respond and restore business services and processes to normal? Hopefully, vulnerability scanning, penetration testing, and patch management will mitigate most incidents from happening in the first place, but if something manages to get through, you need to have a plan that decreases the scope of damage and works to eliminate the cause of the problem. This may include who needs to be looped in during an incident, what teams need to be informed, what automated or manual processes need to happen, and so on.
Vulnerability Management Framework Deployment Techniques
Deploying a vulnerability management framework successfully depends on employing the proper techniques for vulnerability scanning, patch management, penetration testing, and intrusion detection and prevention.
Selecting Vulnerability Scanning and Assessment Tools
When choosing vulnerability scanning and assessment tools, you’ll want to consider what assets you need to scan (servers, mobile devices, web applications, workstations), how big and complex your organization is, and how much detail you need regarding your current security posture. You’ll also want to weigh this against the cost of certain tools and your desired budget.
It’s also generally a good practice to use more than one vulnerability assessment tool to improve the chances that you’ve discovered all potential weaknesses.
Automated Patch Management and Deployment
The more you can automate systems, the more likely they are to be performed. An automated system can be created to scan all devices in the environment, determining which patches are missing in the apps, software, and devices being used. This can help keep everything up-to-date and reduce the likelihood of recent vulnerabilities causing trouble.
Penetration Testing
Penetration tests are non-destructive tests that validate what the vulnerability scans are telling us. A penetration test goes all the way into the infrastructure to the point where it could run the exploit, but it doesn’t. In essence, it simply provides direction that says, for example, these ports are open, this is a known vulnerability for these ports, and these are the tools that hackers might use to exploit these open ports.
While this seems simple, this direction is incredibly helpful. There are over 65,000 ports that could be opened or closed. Some applications require specific ports to be open, so keeping them all shut isn’t a viable option. When you install a piece of software, you may not even know it’s opening a specific port. In short, a vulnerability scan can tell you where to focus your efforts, and penetration testing tells you how much effort to put into closing a vulnerability.
Intrusion Detection and Prevention (IDPS)
An intrusion detection and prevention system (IDPS) can be used for many things, not just vulnerability management. It can also help identify malware, DDoS attacks, unauthorized access, and other intrusions. Scanning with an IDPS can help uncover threats that the system knows about and the organization may not.
Vulnerability Management Framework Challenges
Some challenges can get in the way of implementing a vulnerability management framework, both on an organizational level and on a technical level.
Organizational Challenges
Limitations in staffing, budgeting, or time can make it difficult to implement a comprehensive vulnerability management framework. There may also be resistance from the inside from key stakeholders who are resistant to change.
Technical Challenges
Pulling off a vulnerability management strategy can be time-consuming and complex. Even if your staff has the time, they may lack the technical expertise or specific skillset to implement the framework. Visibility may also be an issue. If the organization doesn’t have visibility on their IT assets with their current technology, they may not be able to identify and prioritize remediation efforts.
3 Tips When Implementing a Vulnerability Management Framework
Your effectiveness at managing vulnerabilities will only be as strong as your policies, procedures, and actual practices. Here are three things to keep in mind when implementing a vulnerability management framework:
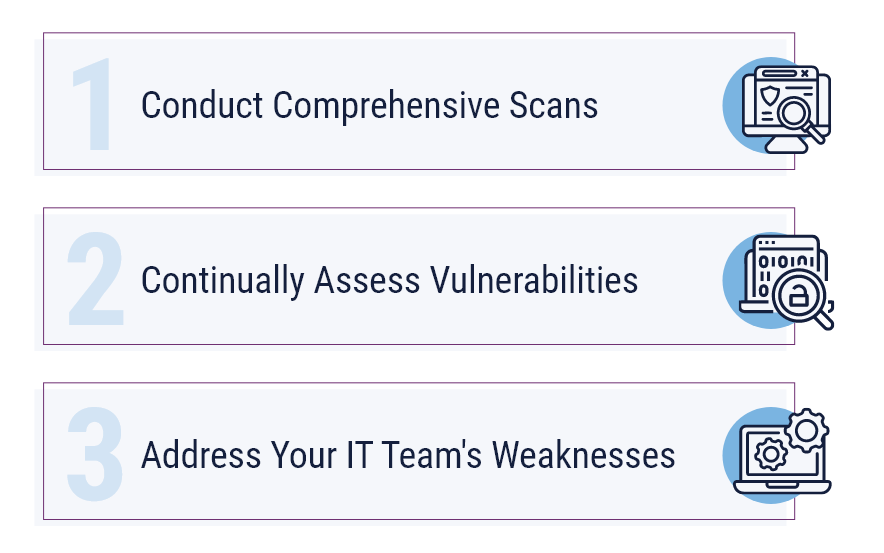
Conduct Comprehensive Scans
Hackers watch vulnerabilities closely. They are aware that a small portion of businesses actually pay attention to them. Vulnerability announcements not only help businesses protect themselves. They also tell hackers exactly what they should try to exploit. Because of this, comprehensive scans are vital.
Scans for a single machine can take an hour and are usually performed in response to a known exploit. We usually run scans for our entire infrastructure over a long weekend. The scan doesn’t affect network performance, but if we start on Friday evening, the scan is usually complete by Sunday morning or Sunday afternoon at the latest. This lets us generate reports first thing Monday morning and get them out to the groups that are in charge of those systems.
Continually Assess Vulnerabilities
As previously mentioned, vulnerability assessments should be a continuous process. Set aside time every 30 days as a best practice for regular assessments, and more if your industry or systems are particularly susceptible to vulnerabilities.
Address Your IT Team’s Weaknesses
IT teams of any size will have knowledge and skill gaps. Most teams feel under-resourced due to daily demands on their time. Identifying what your team has time to do, and what they’re the best at doing, will help you understand where you might need outside assistance.
Get Expert Help Identifying Vulnerabilities with a Managed Security Provider
If you don’t know where your network vulnerabilities are and which ones are most critical, it’s difficult to focus your vulnerability remediation efforts where they can do the most good.
As a managed security provider, TierPoint helps businesses address their biggest cloud and IT security concerns with our secure, reliable, connected IT infrastructure solutions and a nationwide network of 40 data centers. We provide security consulting support to assess, develop and manage a cybersecurity roadmap to minimize risk and implement improvements based on best practices.
As the volume of cybercrime continues to grow, it’s important for organizations to do everything they can to address threats and resolve vulnerabiltiies in order to protect their data and systems. Download our cloud security whitepaper to discover:
- Cloud security threat drivers
- Top threats to cloud security
- The best defenses to protect business from top threats
- And more

