
Table of Contents
If your organization is considering moving to private cloud or you’re trying to decide between cloud platforms, there’s a lot to consider, especially when it comes to security. Private cloud environments can protect the confidentiality, availability, and integrity of your data and applications, but higher levels of customization and control also come with more specific security needs. In this article, we’ll share 10 key components and considerations IT teams should keep in mind for private cloud security.
Introduction to Private Cloud Security
Many businesses migrate to the cloud as part of larger digital transformation efforts. Cloud computing allows businesses to scale their resources more quickly, opens the door to more integrations, and often improves the performance of IT workloads. The vast majority of businesses that are in the cloud have taken on a multicloud strategy, with 70% using at least one public and one private cloud. This mix allows organizations to benefit from the scalability and cost-effectiveness of the public cloud while enjoying the increased control and security of a private cloud. Because businesses often use private clouds to host more sensitive workloads and data, understanding the key components of a robust private cloud security strategy is essential.
What Does Private Cloud Security Mean?
Private cloud security includes any of the methods, technologies, and approaches used to protect applications, infrastructure, and data in a private cloud environment. In a private cloud, computing resources are dedicated to a single organization, enabling greater control over data, configurations, and physical security measures within the data center environment. It also means increased responsibility to ensure workloads are secure.
10 Components of a Private Cloud Security Strategy
Likewise, your private cloud security strategy should focus on the strengths of the environment and incorporate the following components:
- Private Cloud Security Basics
Once the business understands its security responsibilities in the private cloud, it’s important to clearly define data security goals and objectives that work with any compliance requirements, tolerable levels of risk, and general business needs.
From there, an organization can create security policies that determine how people will access and handle data, as well as configure settings in the private cloud. To ensure all components have been considered, the team will need to conduct a detailed inventory of all assets in the private cloud environment, including hardware, software, networking, applications, and storage. - The Importance of Data Encryption
Data should be encrypted when it is being stored (at rest), transferred (in transit), and while in use.
Encrypting data at rest allows it to be protected from incidents like misconfigurations and data breaches. In transit, data can be protected using SSL or TLS protocols. Techniques like tokenization or homomorphic encryption during use protects data while it’s being processed. Businesses also need a key management system to create and store necessary encryption keys. - Access Controls and Identity Management
One of the most secure ways to apply access controls for users is by abiding by the principle of least privilege, allowing the bare minimum of access to users to allow them to perform their business functions and access nothing else.
Strong authentication methods, such as multi-factor authentication, mandate that users take multiple steps to log in. Businesses can also implement zero trust architecture, which goes beyond authentication to include continuous verification, microsegmentation, and strict access policies.
To avoid too many complications with the principle of least privilege, organizations can use role-based access control to assign permissions based on core business functions. This improves consistency and cuts down on the time that would be spent assigning roles to individual users. - Regular Security Audits and Assessments
With regular security audits, businesses can catch potential threats before they pose a larger problem. Vulnerability scanning regularly checks for known vulnerabilities and should be conducted on a regular basis, such as monthly or weekly. The frequency will depend on the sensitivity of the data being protected and the intricacy of the system.
To determine where weaknesses may cause an issue, organizations can run penetration testing, simulating an attack to see how the security controls will fare. Teams can also regularly monitor security logs and review security configurations to ensure they are abiding by best practices and activity is occurring as expected in the environment. - The Role of Firewalls and Network Security
Firewalls can serve as an extra line of defense for your private cloud’s network security. Network segmentation allows a business to divide its private cloud network into parts. This way, if a security breach occurs, the damage is less widespread. Firewalls can also be implemented at network perimeters to control the flow of traffic.
Intrusion detection and prevention systems (IDPS) are designed to survey the network for signs of malicious activity and can automatically block or send alerts when threats appear.
It’s also important to remember the basics. Configure your network devices properly, including routers and switches, to reduce attack surfaces. - Implementing Backup and Disaster Recovery Plans
Even with preventative safeguards in the cloud, things can go wrong. Establish regular data backups to protect against unforeseen issues, including natural disasters, emerging threats, and malicious insiders. Backups should be stored in a geographically separate location and tested regularly to confirm they will work in an emergency situation. Each business will have different recovery time objectives and recovery point objectives (RTO and RPO) — tolerance for how quickly systems need to be back up and running and how much data can be lost. Determine these to decide which backup solutions work for your organization. - Monitoring and Incident Response Plans
Real-time monitoring can also protect against security events and anomalies. Organizations can add a security information and event management (SIEM) system to collect and review security logs to find threats. Before an incident occurs, businesses should have an incident response plan for how to handle security incidents. This includes an approach for how to find, contain, remove, and recover from an incident, as well as notes on improvements to make for next time. - Compliance with Industry Regulations
Industry regulations and compliance frameworks are generally based on the industry and the type of data your business is processing. Most commonly, regulatory frameworks will come into play when organizations are handling sensitive information. Technical and administrative controls should be enacted within the private cloud that meet your organization’s regulatory needs. You should also conduct regular compliance audits to ensure all security controls are meeting necessary standards. - Automation and Security Tools for Private Cloud
While some private cloud security measures require human intervention, others can be automated. Teams may choose to automate tasks, including vulnerability scanning, configuration management, and incident response measures, to save time and allow for greater focus on more critical or strategic initiatives.
There are many security tools that can be incorporated into a cloud environment, including cloud security posture management (CSPM), but it’s also important to stay tapped into trends around emerging threats by incorporating threat intelligence feeds into your monitoring and analysis processes. - Vendor Management and Third-Party Considerations
Managing private cloud security means that a business has to consider many different tools, components, and entry points at once. Third-party vendors can provide security services to lighten the burden, but it’s important to understand their credentials and the scope of their offerings before signing a service level agreement (SLA) with them.
Best Practices for Maintaining Private Cloud Security Maintenance
Implementation is just the beginning, and often the easiest, part of your organization’s private cloud security journey. Ongoing maintenance requires continuous effort and attention to security best practices.
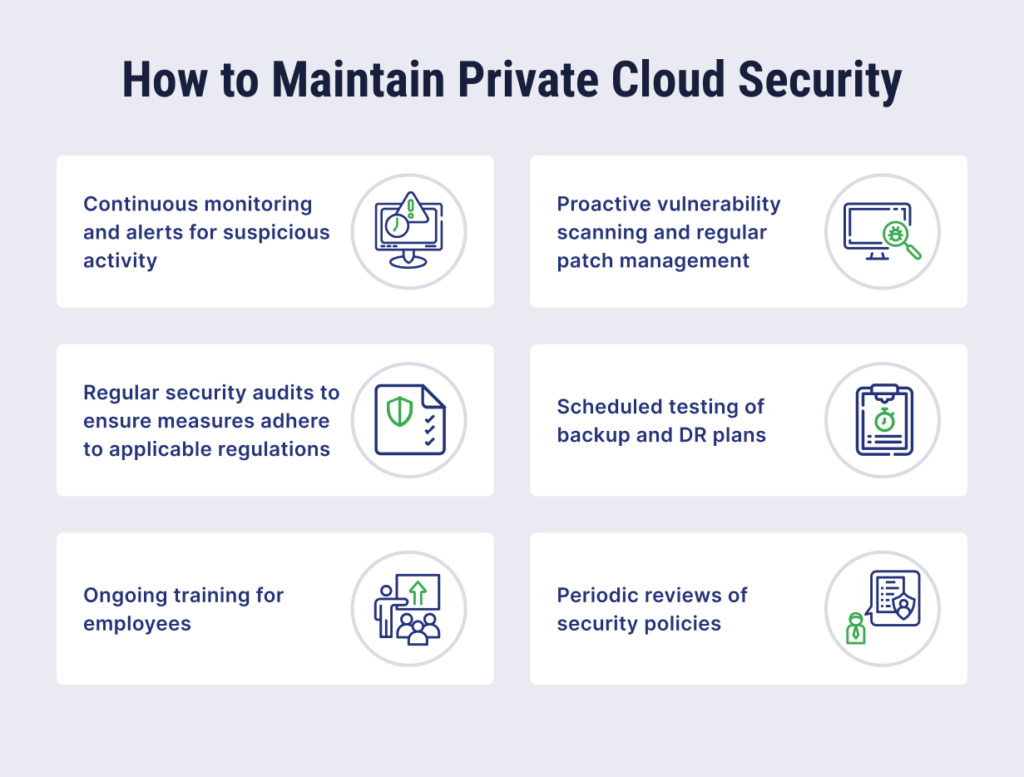
Key tasks should include:
- Continuous monitoring and alerts for suspicious and anomalous activity
- Proactive vulnerability scanning and regular patch management
- Regular security audits to ensure measures adhere to applicable regulations
- Scheduled testing of backup and disaster recovery plans
- Ongoing training for employees
- Periodic reviews of security policies
Next Steps for Protecting Your Company’s Data in the Cloud
Your move into a private cloud environment doesn’t have to saddle you with all of the responsibility. Whether you’re deploying a private cloud, a hybrid solution, or both, a trusted managed services provider like TierPoint can help you along the way. We deliver hosted private cloud and hybrid cloud services tailored to your business needs—balancing uptime, performance, isolation, security, and regulatory compliance. Let us help you build a more secure, resilient, and scalable cloud environment that supports your long-term goals. Schedule a consultation today.

Table of Contents
-
Cloud
Mar 4, 2026 | by Kerri Padgett
Digital Infrastructure Trends to Watch in 2026
VIEW MORE -
Cloud
Feb 27, 2026 | by Mikael Grondahl
5 Data Management Trends to Watch in 2026
VIEW MORE -
Artificial Intelligence (AI)
Feb 11, 2026 | by Mikael Grondahl
Top Trends for AI in Data Management in 2026
VIEW MORE
